Secure, Custom Container Images
From the base layer to app dependencies, ActiveState’s secure containers offer complete customization, full provenance, and none of the patching chaos.







Stop managing third-party code. Start running secure containers.
Spend More Time building
Stop the costly cycle of patching and remediation, and spend your development cycles writing business-critical code.
Stay Secure
Curate a secure, regularly updated open source repository to improve your security posture and create a scalable path to production for your applications.
Simplify Compliance
Use secure, custom containers to easily achieve and maintain complex compliance requirements without lengthy audit cycles.
Customize without compromise
Prevent vulnerable packages from entering your environment. Use over 40 million secure components to customize a container image that mitigates vulnerabilities across every layer of your container. You’ll get your container back with low-to-no CVEs, rebuilt from the base OS through every app dependency.
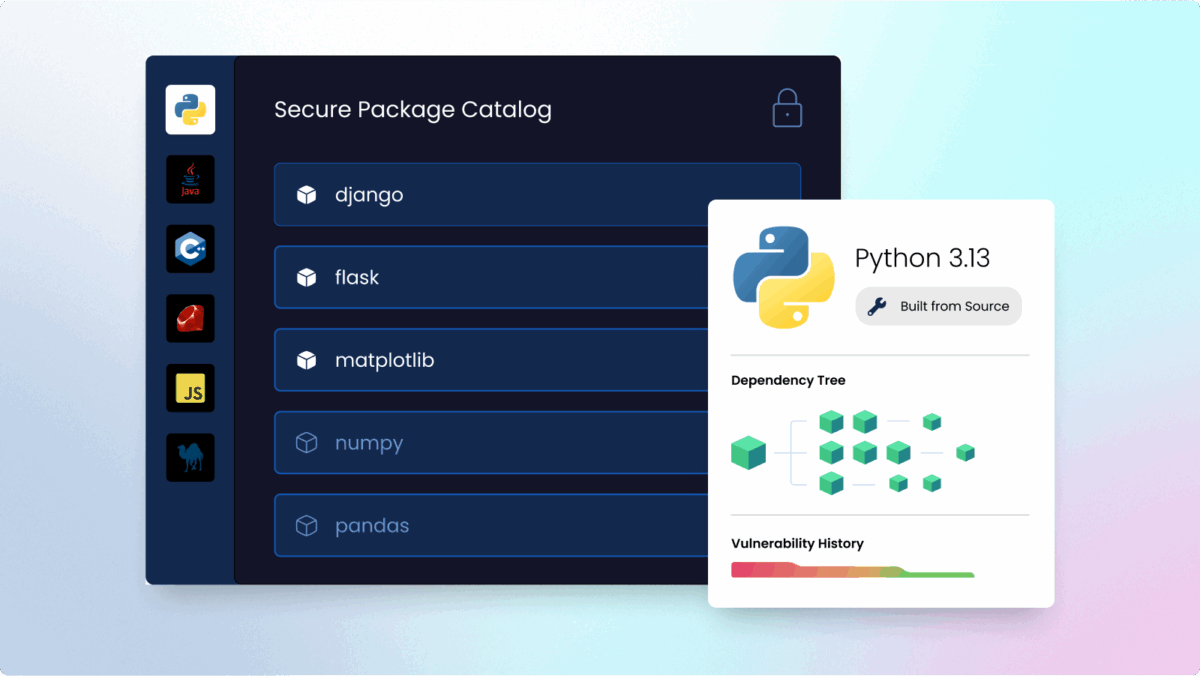
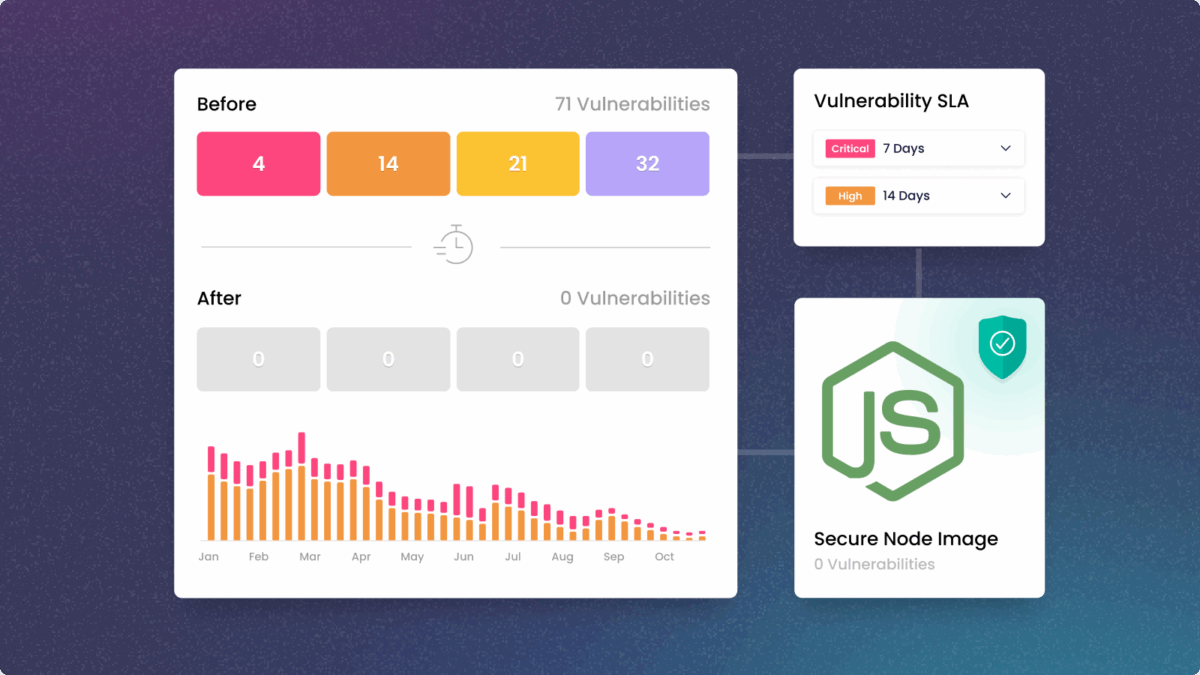
Battle tested build automation
Offload the process of building and maintaining custom images. Inherit the benefits of a secure, automated SLSA-3 build system to perform image customization with a standard remediation SLA of 7 days for critical CVEs and 14 days for all others.
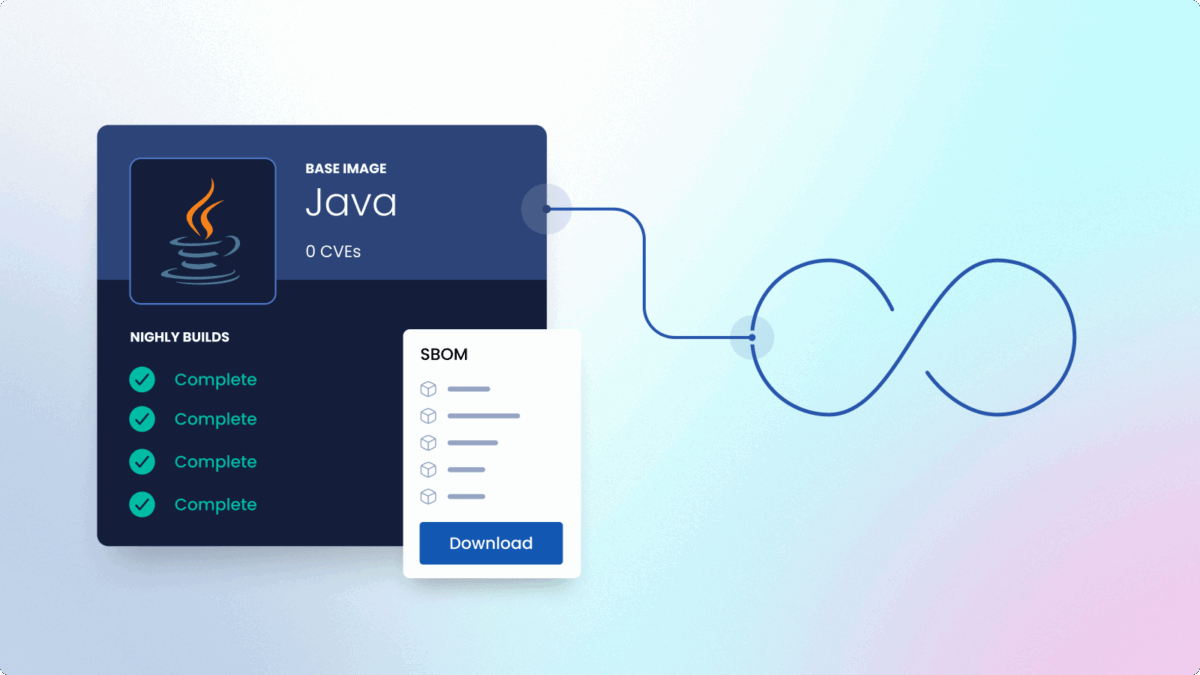
Secure base images, rebuilt daily
Plug-in-and-play minimal, secure container images slot right into your CI/CD pipeline and provide a secure foundation for customization. Each image includes a signed SBOM and is rebuilt nightly to secure your workloads.
What to Expect

Meet the Team
Together with your team, we’ll learn more about your needs and review the requirements of your container.
We'll Handle the Build
From there, the ActiveState team will do the heavy lifting; we’ll build your container based off of your specifications.
Deploy to Production
All that’s left for you to do is to pull your container, watch your CVE count drop, and get it ready for deployment




FAQs
What makes ActiveState containers more secure than standard base images?
ActiveState container images are assembled entirely from source to ensure low-to-no CVEs right out of the box.
Each image is rebuilt nightly and includes a signed SBOM and attestation.
Can I customize the container to fit my specific tech stack?
Yes. Any of our free containers can be further customized in collaboration with our Customer Success team. Customization leverages ActiveState’s catalog of 40M+ secure components, ensuring a secure container from the ground up.
How fast can I get a custom container back?
In most cases, your secure container will be delivered via a private repository for evaluation within a few business days. Specific timelines will be scoped based on your application requirements.
Do ActiveState containers help with compliance?
Absolutely. Available on demand, ActiveState container images can be further hardened to support strict compliance requirements (e.g., SOC 2, FedRAMP, etc.).