With twice as many software supply chain attacks this year as the last three years combined, 2023 was the year the software supply chain threat got real, costing businesses $46B to address 245K supply chain incidents.
In line with these staggering numbers, the Application Security Posture Management (ASPM) 2024 report, which surveyed 500 US-based CISOs, found that 77% of CISOs perceive software supply chain security as a blind spot for AppSec.
The problem is that AppSec continues to be narrowly focused on vulnerabilities, rather than the much wider threat of malware. To be sure, vulnerabilities continued to increase in 2023, but they were eclipsed by the exponential growth of supply chain attacks, primarily originating as malware.
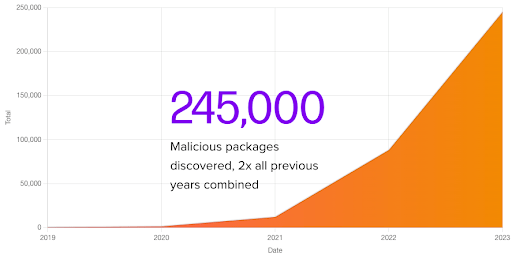
Source: Sonatype
Malware, or “malicious software” is a catch-all category of threats that include everything from viruses and worms to trojans and backdoors to spyware, all of which are designed to provide hackers with a potential weak point they can exploit to gain unauthorized access to an organization’s data and systems.
There’s nothing new about malware, which has been around since the era of Bulletin Board Systems (BBSs), predating the internet. What is new is the distribution method. Namely, by compromising open source code included in a popular software application, hackers can have their malware hitch a ride to all of that software’s customers/users. Now, instead of randomly looking for a weak point, hackers can use their own exploit to steal data, install harmful software, gain control of a network, or otherwise compromise an organization’s software or hardware. And they’ve been quite successful in 2023.
Software Supply Chain Attacks in 2023
Hackers have taken advantage of weaknesses in the software supply chain to perpetrate some wide ranging software supply chain attacks during 2023. While security has been focused on patching the zero-day vulnerabilities ransomware groups prefer to exploit, they’ve deprioritized the risks inherent in their software supply chain.
Some of the most significant attacks during 2023 include:
- 3CX – is a well-known provider of VoIP software. In April, a software supply chain attack struck 3CX’s Mac and Windows client apps, impacting 600,000 users. This month-long, state-actor-led attack prompted 3CX to urge users to uninstall compromised apps and migrate to safer frameworks.
- MOVEit – Progress provides MOVEit Transfer, which is managed file transfer software. In June, a vulnerability led to a gigantic chain of record-breaking breaches affecting >1000 businesses and >60M individuals, eventually costing businesses >$9.9B in damages.
- SHCG (Shields Health Care Group) provides medical imaging, radiation oncology, MRI, PET and CT scans, as well as other imaging services on behalf of healthcare providers. In April, SHCG suffered a cyber attack that exfiltrated the information of >2M patients, including their SSN and patient ID.
- NCB Management Services, a US-based debt collector, suffered a cyber attack that exposed the financial information of nearly 1.1M people. In April, NCB disclosed that hackers had accessed credit card data for Bank of America past-due accounts. Apparently, NCB eventually paid a ransom to prevent the data ending up for sale on the dark web.
- Latitude Financial is a Melbourne-based financial services company that provides personal loans and credit cards to customers in Australia and New Zealand. In March, Latitude was subject to a cyber-attack that resulted in the theft of 14M customer records containing personal information.
This above is a greatly abbreviated list of cyber attacks and data breaches, none of which show any sign of slowing down in 2024.
Government bodies have taken notice, and have been busy creating a regulatory landscape to encourage, and ultimately impose penalties on software vendors that can’t or won’t deal with their software supply chain threat.
Software Supply Chain Legislation in 2023
Two of the industry’s best “worst practices” never seem to change from year to year, namely:
- 79% of codebases are never updated once created.
- 2.1 billion OSS downloads (the same number as in 2022) had known vulnerabilities, but up to 96% of them could have been avoided because a better, fixed version was available.
It’s these kinds of practices that governments worldwide are looking to curb by introducing a number of different pieces of supply chain security legislation, many of which came into effect during 2023, including:
- In March, the US government passed the Securing Open Source Software Act of 2023, which establishes the duties of the Director of the Cybersecurity and Infrastructure Security Agency (CISA) regarding open source software security.
- In July 2023, the SEC adopted new rules forcing publicly listed companies to disclose significant cybersecurity incidents. They must also provide annual cybersecurity risk management, strategy, and governance information, with comparable requirements for foreign private issuers. The rules went into effect December 15.
- In August, the German Federal Office for Information Security (BSI) published its requirements for the creation of SBOMs aimed at enhancing the ability of consumers to better understand and manage the potential risks of the software they use.
- In September, the Australian Signals Directorate issued Guidelines for Software Development, incorporating multiple provisions around various aspects of secure software development. A proposed control requiring the creation and distribution of SBOMs to consumers of software is among the more than 30 recommendations made by the guidelines.
- On October 1, the FDA started enforcing their mandate that all medical device manufacturers must create and maintain a software bill of materials (SBOM).
While much of the legislation is aimed at establishing best practices, some have begun introducing penalties for non-compliance. The US National Cybersecurity Strategy 2023 is perhaps the most draconian, proposing that software vendors could be sued by their customers for failure to secure and maintain their software.
Conclusions – Software Supply Chain Security in 2024
Bad habits are hard to break, and software bad practices are no different. For example, we’ve been downloading prebuilt packages created by authors with whom we have no relationship from public repositories for over 25 years, and the majority of developers aren’t about to stop doing it anytime soon, despite the growing risks.
The problem lies in the fact that no organization, no matter how large, can hope to close all the weak links in their software supply chain, but hackers only need a single flaw to exploit.
As a result, software supply chain attacks, whether they manifest themselves as data breaches, ransomware or other malicious attacks, are now just another cost of doing business. You can even buy insurance to help defray the financial costs of recovering from an attack and/or being sued by your customers.
At a minimum, however, you can at least ensure you start secure, even if subsequently you rarely update your codebase. This is why ActiveState provides you with a security profile for your codebase BEFORE you build it, enabling you to ensure you aren’t accidentally including vulnerabilities. The ActiveState Platform will then automatically build your runtime environment from vetted source code, ensuring your project starts with a clean, secure codebase.
Next Steps:
Watch our webinar on how to get started securing your software supply chain in 2024.






