Vulnerability management shouldn’t be treated as a ‘set it and forget it’ type of effort. The landscape of cybersecurity threats is ever-evolving. To face the reality of this continuous threat, modern enterprises need a realistic, repeatable process for addressing and remediating vulnerabilities, like the vulnerability management lifecycle.
You don’t need to reinvent the wheel when introducing programmatic vulnerability management to your organization. The vulnerability management lifecycle process provides an excellent, rinse-and-repeat framework nearly any company can customize to their processes and needs. Plus, it’s widely used and well-accepted by leading enterprises as a vulnerability management best practice. In other words, you’re in good company.
In this article, we’ll break down the vulnerability management lifecycle, its key steps, how it relates to broken access control, and how you can begin to implement and automate vulnerability management at your organization.
What is the vulnerability management lifecycle?
The vulnerability management lifecycle (VML) is a cohesive, continuous process that helps companies detect, prioritize, and remediate cyber security threats.
Not only does the vulnerability management framework help you manage existing vulnerabilities within your applications, but it also helps you take a proactive approach to ensuring these vulnerabilities don’t end up there in the first place. It’s a continuous effort, rather than a check-list.
4 key benefits of vulnerability management in cyber security
Before we dig into the vulnerability management process steps, let’s walk through the key benefits of investing in and focusing on vulnerability management.
- Enhance your security posture by reducing your attack surface and managing broken access controls
- Remediate vulnerabilities faster and make strides to improve key metrics, like mean time to detect (MTTD) and mean time to respond (MTTR)
- Strengthen compliance with important industry standards, reducing the potential for costly fines and reputation loss
- Improve operations by streamlining how DevSecOps work together and shifting security left in the development process
What are the vulnerability management lifecycle NIST steps?
When it comes to implementing the vulnerability management lifecycle, many companies opt for the National Institute of Technology (NIST) cybersecurity framework (CSF) for vulnerability management.
In February 2024, the NIST updated its long-standing The NIST Cybersecurity Framework recommendations to keep up with current cybersecurity challenges. The 2.0 version of the document outlines the NIST approach, providing a methodical means for companies to understand and assess their cybersecurity posture, prioritize risks, and communicate cybersecurity topics effectively inside and outside an organization.
Based on the NIST CSF framework, the vulnerability management lifecycle includes six steps or “core functions”: govern, identify, protect, detect, respond, and recover. The importance of these steps is to be determined by each company’s needs and can be completed in any order.
(P.S. This framework has some overlap with the application security posture management (ASPM) framework pillars: detect, prioritize, and remediate. Think of the NIST vulnerability management lifecycle as a reliable, powerful, and tactical approach for how your team can implement ASPM. The three pillars of ASPM can all exist within the NIST CSF.)
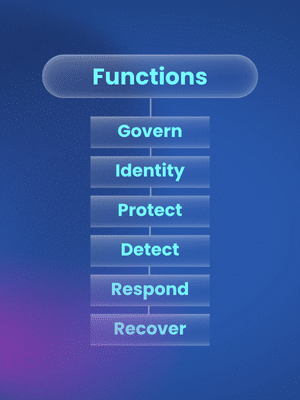
Function 1: Govern
The Govern function within the NIST CSF framework sets an organization up for success with its cybersecurity efforts. It addresses the current context within the organization, helping to establish roles and responsibilities, authorities and decision makers, policy, processes, and oversight. This function is critical for ensuring cybersecurity efforts are upheld and prioritized across the organization.
Function 2: Identify
Understanding and taking inventory of all of your organization’s assets is an important step towards prioritizing the most critical vulnerabilities first. According to the NIST CSF, assets to take inventory of include:
- Data
- Hardware
- Software
- Systems
- Facilities
- Services
- People
You should also take steps to identify all your suppliers and other related cybersecurity risks. It’s also recommended that under the Identify function, you identify opportunities for improvement within your company’s cybersecurity program. It’s important to know where your current strengths and weaknesses are.
Function 3: Protect
The Protect function focuses on protecting the assets that have been identified and prioritized, reducing the potential impact or likelihood of a breach. Making progress within this function could look like fixing broken access control (more on this later), improving identity management, further securing identity management, implementing training programs, and bolstering platform and data security.
Function 4: Detect
The Detect function focuses on identifying and analyzing potential cybersecurity attacks or opportunities for compromises. The Detect function enables the speedy discovery of anomalies that indicate vulnerabilities are being exploited by bad actors. Detection is a critical step in ensuring prompt incident response and recovery.
Function 5: Respond
Within the Respond function, teams take action to mitigate and remediate cyber security attacks discovered during the Detect function. Actions could include incident management, communication, reporting, and analysis.
Function 6: Recover
The Recover function focuses on restoring assets and operations that may have been compromised by an attack, helping DevSecOps teams return to ‘business as usual’ as fast as possible.
Broken access control: A threat to your enterprise vulnerability remediation process
In our recent report, 2025 State of Vulnerability Management & Remediation, we discovered that broken access controls are one of the most prevalent vulnerabilities now faced by organizations.
Implementing the vulnerability management lifecycle in your organizations is all well and good, but if you’re leaving the door open to bad actors through broken access control, you’ll never close the loop. With development teams using an increasing amount of open source and GenAI code to build their apps, there’s even more potential for broken access controls to unknowingly slip through the cracks. This opens companies up to customer and company data breaches, compliance issues, and potential reputation damage.
How do you manage broken access controls, accurately determine which vulnerabilities to prioritize, and find the best path to remediation? Incorporating vulnerability remediation and penetration scanning within your vulnerability remediation process is important for prioritization and remediation.
The two are a powerful combo Vulnerability scanning will help you detect and prioritize existing weaknesses within your apps. Then, penetration testing can help you put those weaknesses to the test by simulating real-world attacks to determine the potential impact and likelihood of an attack. Penetration testing helps teams predict and prioritize which vulnerabilities to remediate first and how to approach fixes.
As part of your vulnerability lifecycle management efforts, an intelligent remediation platform like ActiveState can help you gain continuous visibility into potential open source vulnerabilities and their impact without overloading your team by automating the discovery, prioritization, and remediation of these risks. ActiveState’s platform helps you understand the true extent of your risk, prioritizes what to fix first, and delivers remediated open source packages right to your desktop, allowing your teams to focus on innovation rather than being overwhelmed by potential impact.
Pair this with popular penetration testing tools like network scanners (Burp Suite), web application proxies (Network Mapper), and vulnerability scanners (Nikto). and you’re well on your way to improving your security posture.
How to implement and automate the vulnerability management lifecycle in your organization
Where do you begin if you’re interested in introducing a more structured approach to the vulnerability management lifecycle at your organization?
DevSecOps teams are overloaded with both tactical and strategic work, which can make it seem challenging to introduce change and new processes. The good news is, vulnerability remediation tools have come a long way. Powered by automation and AI, Vulnerability Management as a Service (VMaaS) solutions have the features you need to help you implement ASPM and the vulnerability management lifecycle at your organization.
ActiveState’s end-to-end Vulnerability Management as a Service solution combines Application Security Posture Management (ASPM) and Intelligent Remediation capabilities with expert guidance. This enables DevSecOps teams to not only identify vulnerabilities in open source packages, but also automatically prioritize, remediate, and deploy fixes into production without breaking changes. Automating security processes ensures you’re focusing on the most impactful fixes first, reducing human error and increasing incident response times.
VMaaS and intelligent remediation tools help you keep on top of your vulnerability remediation process by:
- Performing continuous vulnerability scanning
- Conducting risk-based prioritization based on ongoing threat intelligence
- Automating remediation and patching within your existing DevSecOps workflows
- Ensuring compliance and safety reporting
In review: Why the vulnerability management lifecycle is important for enterprises
Implementing a structured vulnerability management lifecycle is essential for maintaining proactive cybersecurity in modern enterprises. Following a clear and repeatable framework helps enterprises detect, prioritize, and remediate security risks faster and more efficiently.
A well-defined vulnerability remediation process, enhanced by cyber threat intelligence, strengthens your security posture by enabling you to address vulnerabilities before they escalate. Risk-based prioritization is especially crucial, allowing organizations to focus on the most impactful threats first.
Automating security processes with AI-powered intelligent remediation tools further enhances vulnerability management. Automation reduces human error, streamlines responses, and accelerates remediation timelines, ensuring your organization can act swiftly and effectively against evolving threats. By embracing these practices and tools, enterprises can move from a reactive security stance to a proactive, resilient cybersecurity posture, safeguarding both their assets and their reputation.
ActiveState provides secure, hardened open-source packages that help DevSecOps and security teams minimize vulnerabilities in enterprise application development.
Download the 2025 State of Vulnerability Management & Remediation Report.







