As microservices have reshaped application design, containers have become the go-to way to package and deploy workloads. They are fast, lightweight, and highly scalable, making them the ideal choice for cloud-native teams. In fact, nearly 90 percent of organizations report that at least some of their applications run in containers, and this number is likely to grow with the rapid adoption of emerging workloads such as generative AI.
However, this popularity comes with a downside. Containers do not remove the security risks that come with open source software, and in many cases, they can make those risks easier to distribute. Each image contains its own operating system components, libraries, and packages, meaning each image carries an attack surface, and with it, vulnerabilities that malicious actors can exploit.
In reality, most organizations run containers with some level of known risk. The challenge is figuring out how to reduce that risk while keeping developers productive. Hardened container images provide a way to meet that challenge.
The Container Status Quo
When a new container is needed, many developers head straight to Docker Hub. It’s the world’s largest repository of container images, offering both community-contributed images and a curated set of “Docker Official” images.
On the surface, these official images seem like a safe bet. They’re popular, regularly updated, and widely adopted. But “official” doesn’t mean “free from vulnerabilities.” Even images from trusted sources can ship with CVEs.
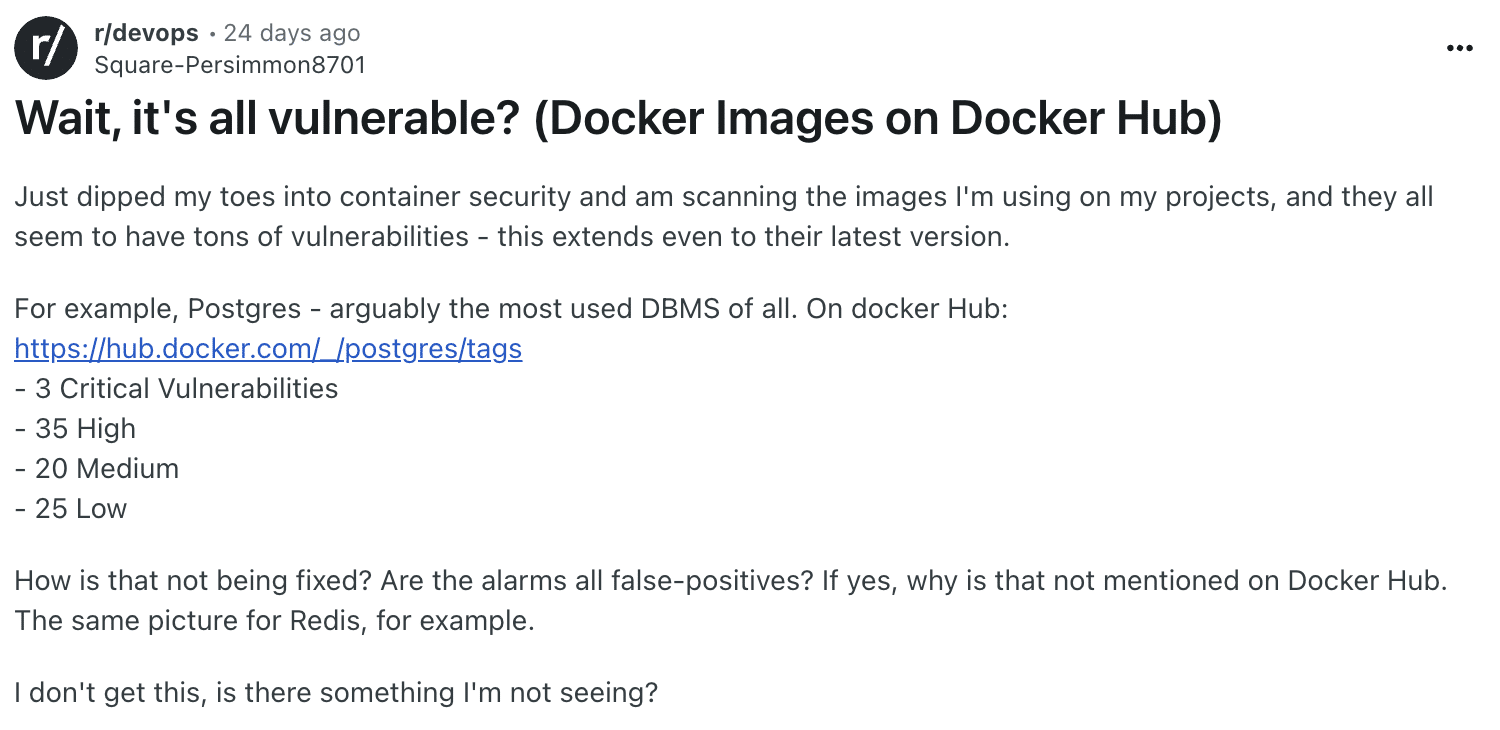
Here’s where the status quo starts to break down:
- If your team scans an image with an SCA tool like Trivy or Grype, you might find dozens (or even hundreds) of CVEs.
- Some of those findings will be false positives or irrelevant in your runtime environment. Others will be real risks.
- It’s up to your team to sort through them, decide which are exploitable, and remediate what matters most.
That’s assuming a scan happens at all before an image is pulled into your environment. If a developer grabs an image and starts building on top of it without reviewing vulnerabilities, you’ve just inherited those risks.
Common Security Challenges in Container Management
A reactive approach to container security (detect, prioritize, patch, repeat) drains developer time, slows down delivery cycles, and if managed poorly, can open the door to serious breaches. Here are some potential threats.
Challenge 1: Vulnerable Base Images in Production:
A dev team at a fintech organization builds all their services from a public python: 3.10-slim base image and pushes their images to prod without comprehensive image scanning. Two months later, a critical OpenSSL vulnerability is discovered which allows remote code execution. Attackers start mass-scanning for this CVE and within hours an exposed pod is exploited, giving shell access inside the container to the attacker.
Challenge 2: Misconfigured Containers Expose Internal API:
A retail company deploys Go-based backend in Docker with the containers started as root, with ports exposed directly via a node port service. During debugging, a developer enables an internal admin endpoint /debug/pprof and leaves it on, protected only by a static token baked into the image. A routine external scan finds the open port and the predictable token in the image’s environment variables, allowing an attacker to access data from the service.
These examples illustrate only a small sample of the container security issues that can arise from a reactive approach. Fortunately there is a way to get ahead.
The Strategic Role of Container Hardening
Container hardening offers a way to break that cycle. While exact definitions vary, the practice generally includes the combination of two strategies:
- Minimization: This involves removing everything the container does not need, including unused libraries and unnecessary operating system components. Doing this reduces the attack surface and can make the image smaller and faster to deploy. For example, replacing a full Ubuntu base image with a minimal glibc-only environment.
- Configuration for security: This involves adjusting settings, permissions, and build processes to make exploitation more difficult. This can mean running as a non-root user, using a read-only filesystem, or signing images so you can later verify where they came from.
In addition to minimization and configuration, a variety of other best practices are frequently also applied to ensure security is baked into the beginning of the container lifecycle. These include:
Building from trusted sources: Every package, library, and dependency should come from a verifiable, reproducible source. Provenance makes it easier to respond quickly when a vulnerability is disclosed because you can trace exactly where the component came from and how it was built.
Embedded visibility: Generating a signed software bill of materials (SBOM) during the build creates a permanent record of everything inside the container, including version numbers and license details. This SBOM can be used for compliance audits, vulnerability scans, or customer assurance without needing to reverse-engineer the image later.
Enforcing policies in the pipeline: Set rules that the build process must follow before an image can be published. These can include automated vulnerability scans, image signing, and compliance checks. By enforcing these policies automatically, you ensure that only secure, compliant containers reach production.
In short, a hardened container should:
- Include only the necessary components required for the desired use case.
- Exclude shells and mutable files to prevent unauthorized changes at runtime.
- Use only packages built from vetted, reproducible sources.
- Include SBOMS, attestations, signing, and other checks.
- Have low-to-no CVEs before deployment, with any remaining findings documented as false positives or unreachable code.
The result is an image that begins with fewer vulnerabilities, is designed to resist compromise, and has been developed with security in mind from the beginning of its lifecycle. By enforcing these policies automatically, you ensure that only secure, compliant containers reach production.
For many organizations, container hardening also provides a way to meet (and retain) regulatory requirements, avoiding costly retrofits later. Compliance frameworks often set the baseline for how cryptographic modules are configured, how vulnerabilities are addressed, and how artifacts are documented. If these requirements are met during the build process, teams can avoid costly rework and reduce the risk of non-compliance penalties. They can also move faster when an audit or customer security review takes place.
Container hardening and vulnerability management: Why automation is the answer
Even the most carefully assembled hardened container will not stay secure forever. New vulnerabilities are disclosed every week, and without an automated process for finding and fixing them, teams risk running outdated images in production.
Manual checks can work in small environments, but they do not scale when dozens or hundreds of containers are in active deployment. Automation is the key to keeping pace.
Automate vulnerability detection and remediation –Integrate automated scanning tools directly into your build and deployment pipelines. This ensures that every image is checked before it reaches production. Using multiple scanners increases coverage, as each may catch issues the other misses.
Close the gap between detection and remediation – Automation should not stop at scanning. In some cases build processes can automatically apply security patches, swap out vulnerable package versions, or rebuild images from updated base layers. For any vulnerabilities that cannot be immediately fixed, automated workflows should log them, document the risk, and tag the image so teams can track and address them later. Providers of hardened images, make it easy to simply point your CI/CD platform at a repository and pull an always up-to-date version of your container image in deployment.
Enforce hardening standards at every build – Automated policies can block any image that does not meet predefined security benchmarks. These policies might include the presence of a signed SBOM, passing a hardening scan such as OpenSCAP, or having no critical vulnerabilities detected. Enforcing these checks before images are pushed to a registry prevents weak or non-compliant containers from ever being deployed.
By making hardening and remediation part of the CI/CD pipeline, security becomes a background process that runs continuously without slowing down development. This keeps teams focused on delivering new features while maintaining a consistent security posture across all environments.
How ActiveState Containers Mitigate Security Threats
Returning quickly to the container security challenges outlined above, ActiveState Secure Containers can help your team skip the toil associated with container security and automation.
Vulnerable Base Images in Production –ActiveState Solution:
ActiveState Secure Containers leverage a custom distroless base layer that acts as the foundation for all other ActiveState images. Instead of packaging a complete Linux distribution with its supporting utilities and libraries, our base includes only what’s absolutely required to support the application. No shell, no package managers and no debugging tools. In addition, this base is kept updated by the ActiveState team ensuring it is always patched with the latest update. The result is fewer CVEs, less attack surface and virtually no maintenance.
Misconfigured Containers Exposes Internal API – ActiveState Solution:
In addition to the minimization work that is done on every ActiveState Container. ActiveState applies secure defaults, restricted permissions, and careful configuration to make it harder for attackers to gain a foothold.
Taking the next steps toward container hardening
Building and maintaining hardened containers is a continuous practice that works best when security is treated as part of the development lifecycle rather than a separate checkpoint. That starts with a strong foundation. Use minimal, verified base images stored in an internal registry, update them regularly, and rebuild from these trusted sources whenever new vulnerabilities are disclosed.
From there, make security an automatic part of your build process. Integrate vulnerability scanning, SBOM generation, image signing, and compliance checks directly into your CI/CD pipeline so they run every time an image is built. Automation ensures these safeguards happen consistently, without relying on manual intervention, and helps development teams maintain speed while reducing risk.
Finally, keep improving! Maintain a feedback loop between development and security teams so findings lead to lasting changes in how containers are built and deployed.
As you do this, be sure to track metrics like vulnerability counts, remediation times, and compliance pass rates to measure progress. The result is an environment where hardened containers are the norm, security incidents are less disruptive, and production releases are more reliable.
To learn more about the strategic role of hardened containers, explore our Container Security solutions or contact us today.