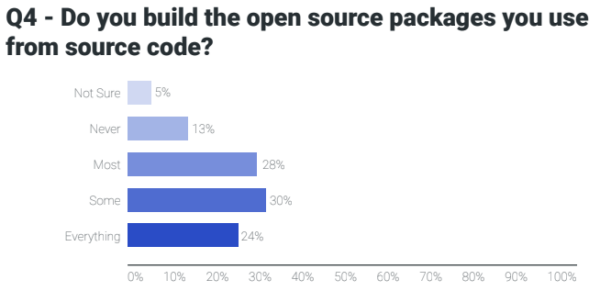
For some organizations, publicly available “community” Python is safe enough for their needs. On the other hand, some security-conscious organizations must not only source secure Python, but be able to prove it using a mechanism like software attestations. In fact, the White House has recently (March 2024) required secure software attestations in order to ensure Federal contractors provide secure products to the Federal government.
At ActiveState, we’ve seen the need to support each of these use cases. That’s why we’re making significant changes this year (besides our long-term CEO retiring) that will result in users on the Free Tier experiencing projects successfully building more frequently.
Building open source packages from source code is complicated, especially as new versions are constantly being released. Each release may introduce:
- New dependencies
- New versions of transitive dependencies
- New compiler flags
- New header files
- A different build order for dependencies
- New methods for binding linked libraries
And so on. Keeping up with changes across the hundreds of open source project releases on a weekly basis is an uphill battle.
As a result, we’ve made the shift to providing community-built packages for Free Tier users, starting with Python. This change offers a number of benefits:
- Faster Builds – compared to the time it takes for a secure build environment to be spun up and all components built from scratch, the time it takes to package community binaries for use with the State Tool is minimal.
- Better Build Success – legacy packages, complex packages, and packages that existed only in binary format (i.e., with no source code provided) will be much less likely to cause build errors.
- Greater Convenience – the ActiveState Platform will continue to package a compatible set of community dependencies into a runtime environment for your project that can be deployed with a single command into a virtual directory by default using the State Tool.
While including community binaries in your project is convenient, they do introduce a level of risk when it comes to your project’s cybersecurity. For example, the ActiveState Platform will continue to produce software attestations for your project, but they will typically indicate SLSA Build Level 0, meaning that we have no information about whether the binary was built in a secure manner or not.
For those that want to decrease the security risk of working with prebuilt dependencies, we recommend the ActiveState Platform’s Team Tier.
Critical Dependencies Automatically Built from Source
Most organizations don’t build all their open source dependencies from source code:
Instead, they select a few key dependencies (such as OpenSSL) to build from source code in order to minimize risk, but are happy to trade off security for convenience when it comes to other packages.
If this sounds like your organization, the ActiveState Platform’s Team Tier is the best place to start. Here, all the standard Python libraries are built from source code, including OpenSSL, zlib, sqlite, ncurses and many more.
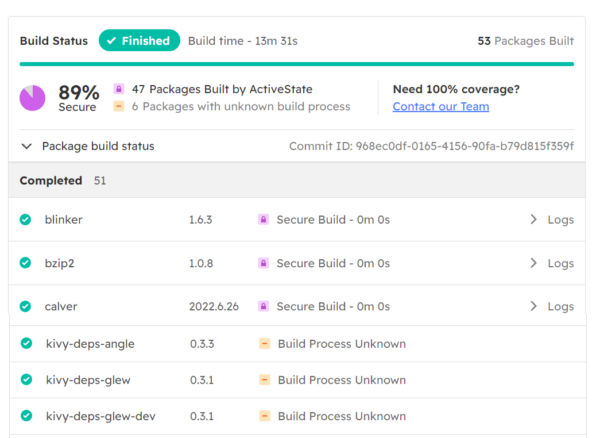
Depending on which packages you select, many of them may also be built from source code, as well. Other libraries will be pulled in prebuilt directly from the ecosystem’s standard repository, starting with the Python Package Index (PyPI). As a result, you may see something like the following screenshot under the Download Builds tab:
In this case, the ActiveState Platform chose to pull in some dependencies directly from PyPI, most likely due to the difficulty/failure of the build process. The individual software attestations generated for this project will reflect their source and build process:
- Dependencies denoted as “Secure Build” will have a SLSA Build Level 3, indicating that it was built on a hardened build platform that offers strong tamper protection.
- Dependencies denoted as “Build Process Unknown” will be assigned a SLSA Build Level 0, indicating that the build process is unknown.
- For the overall runtime environment, the software attestation is likely to indicate a SLSA Build Level 1, indicating that provenance does exist, but is imperfect.
If your organization needs to prove a high level of supply chain security for your open source components in order to comply with regulatory or industry requirements, we recommend the ActiveState Platform’s Enterprise Tier.
Ensuring Software Supply Chain Security
Ensuring the security and integrity of the open source components in use across the software development lifecycle is key to some security-conscious organizations. In practice, this means being able to do:
- Verify the provenance (i.e., origin) of all open source dependencies.
- Securely compile, build and/or package dependencies using a hardened build system that’s resistant to tampering.
- Verify the integrity and security of any software artifact produced or consumed during the software development process.
The Enterprise Tier of the ActiveState Platform ensures that all open source dependencies (including linked C or Fortran libraries) are securely built from source code using a SLSA-compliant hardened build service. As a result, automatically generated software attestations will be issued to prove that each dependency, as well as the overall runtime are rated “SLSA Build Level 3.”
In cases where dependencies fail to build for Enterprise customers, our build engineers will investigate the failure, resolve the issue and update the project.
Conclusions – Open Source Security Risk Is Your Choice
No matter your appetite for software supply chain security risk, the ActiveState Platform has an appropriate solution. There are organizations for whom innovation trumps security, which is seen (rightly or wrongly) as slowing down developers. Other organizations prioritize security and have little appetite for risk, but the majority fall somewhere in between.
Whatever your stance – and whatever your use case – the ActiveState Platform has a solution. More importantly, it allows you to evolve your stance over time as security becomes more important to your customers.
For example, it’s predicted that by 2025, 60% of enterprises will use cybersecurity risk as a key factor when determining which software to purchase and deploy. With more and more cyberattacks continuing to originate from malware within the software supply chain, it’s not a matter of if you’ll be affected, but when. With ActiveState, enhancing your security profile is as easy as upgrading your subscription.
Next Steps:
Learn more about Secure & Community Binaries. Watch our webinar on How SLSA Fires Up Your Software Supply Chain Security: Real World Examples