See what I mean? Those of us in the open source world seemed to fare no better in 2021. Despite cheering the successful flight of an open-source-driven helicopter on Mars, we’ve been plagued with an eight year old critical vulnerability in Java’s Log4J, reminded of just how much Python 2 is still out there and even upbraided by President Biden himself.
But there are lessons to be learned from 2021 as we plan for 2022. Here are the stories from the past year that can help you put your best foot forward in the coming year.
Python 2 Still in the Supply Chain
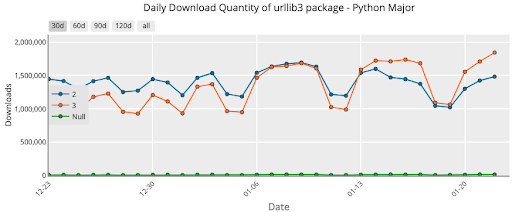
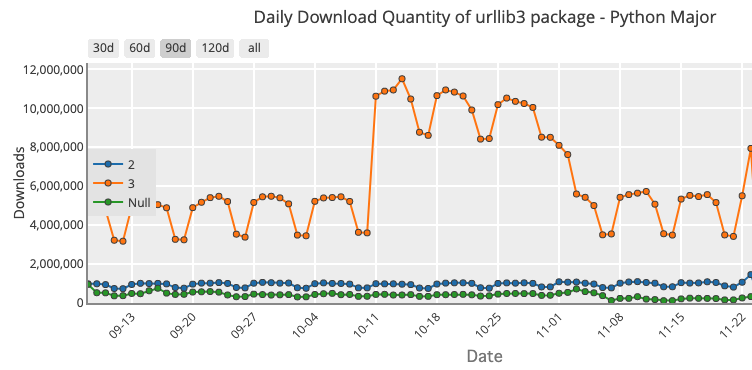
Python 2 was officially sunset on January 1 2020, but according to PyPIstats.org its use has not decreased even after almost two years. For example, the download volume for the popular package urllib3 has remained unchanged:
Dec 2019 to Jan 2020:
Sept 2021 to Nov 2021:
While the proportion of the Python 2 downloads of urllib3 has gone from ~50% of all downloads two years ago to ~16% today, in absolute terms, daily download volume remains the same at ~1.5M. The implication is that new Python users have adopted Python 3, but older users continue to work with Python 2, which has had numerous critical vulnerabilities logged against it since it went EOL.
Log4J Vulnerability
Even more ubiquitous than Python 2 is the Apache logging library, Log4j, which has been around for much the same length of time, but is in far more widespread use across countless industries both private and public.
The zero-day Log4Shell vulnerability itself has been around since 2013, but was only reported late last year. It promptly received the highest (10.0) Common Vulnerability Scoring System (CVSS) security rating since it enables remote code execution, potentially allowing hackers to gain remote access to sensitive systems and data. Much like with Heartbleed, ShellShock and other widespread critical vulnerabilities before it, software organizations everywhere dropped what they were doing and got to patching.
The good news is that we’re getting much better at addressing critical zero-day vulnerabilities in just a few days, as exemplified by the quick turnaround fix by the Log4J team. But the real significance of these kinds of widespread, critical security flaws is to heighten awareness of cybersecurity among the CxO crowd. Without long-term corporate sponsorship, though, these kinds of cybersecurity fire drills will remain just that–fire drills.
President Biden’s Open Source Security Executive Order
The good news is that open source hit the radar of the President of the United States in 2021. The bad news is that open source HAD to hit the radar of the President of the United States in order to motivate all of us to get better at open source supply chain security. In some ways, though, President Biden may end up being the ultimate corporate sponsor that software organizations can point to in order to finally spend the time and resources to secure our software supply chains.
US President Biden called for bold software changes in response to the dramatic rise in cyber attacks during the pandemic, including some never-before-seen hacks to both physical and software infrastructure. Some of the changes called for are eminently pragmatic, including;
- A Software Bill Of Materials (SBOM) for every software application
- Provenance, or the ability to be able to identify the origin for all software components in any application
- A way to check for and automatically remediate vulnerabilities
Other suggestions describe long standing problems for which practical solutions are still aspirational. But when the President of the United States puts open source security in front of issues like the pandemic, global warming, and the economy, the status quo is no longer tenable and new solutions need to be explored.
Read more about the US Executive Order and how it impacts you.
How Secure is the Software Supply Chain?
Given Biden’s Executive Order and the growing spike in supply chain attacks, we conducted a survey in 2021 of nearly 1500 software professionals who shared with us how secure their use of open source is.
Some key takeaways for 2022 planning include:
- Almost 80% of the organizations surveyed build some or most components from source, but only 22% can create reproducible builds.
Without reproducibility, no built artifact can be deemed secure since there is no way to verify if the source code was compromised when the original build was produced. As a result, these organizations could be using compromised code and never know it until they (or their customers) get hacked. - More than 30% of organizations continue to implicitly trust open source repositories.
Even though open source organizations are making great strides to improve the security of their public repositories, the reality is that they are still the wild west where anything goes. Implicitly trusting open source components from public repositories exposes organizations to security risks, including typosquatting, dependency confusion, and prebuilt binaries that may contain malware. - More than 60% of survey participants scored poorly when it comes to implementing secure supply chain best practices.
Worse, the implementation rate of best-practice security and integrity controls simply does not match the growing supply chain threat. Much more work needs to be done in 2022 to ensure software development organizations and their downstream customers can credibly avoid being compromised by bad actors.
Use our State of software supply chain security survey report to see what are the best practices in the industry that can ensure the security and integrity of a software supply chain.
Open Source Now on Mars
ActiveState has always professed the goal of having an ActiveState solution on every device on every planet. Unfortunately, we missed out on the opportunity of supplying open source to the first-ever Martian helicopter flight which was powered by multiple open source projects from Python to Linux to yes, even Log4J.
The Mars Helicopter ran on a version of F Prime, which is a flight software framework built by JPL for CubeSats, small spacecraft, and instruments. It was open sourced by NASA in 2017 and can be found in its open source catalog,
The helicopter looks more like a passion project than rocket science, being composed of an open-source OS (Linux), open source flight software (F Prime), and commercial parts that you can buy off the shelf, including two cell phone cameras.
Want to build a Mars Helicopter of your own in 2022? Start here.
Looking for a turnkey software supply chain solution in for you and your team in 2022?
The ActiveState Platform is available for developers and professionals to try for free.
Want to get a free demo to see how it works for your security needs? Send a message to our team who can help you better understand our Platform and how it can integrate with your existing workflow. Contact us for a demo