Software vendors of all kinds, big and small, are in the habit of not updating their open source software. For example:
- Microsoft Outlook is still based in part on Perl 5.16, which has been EOL since 2013.
- Java 8, now 10 years after its first release in 2014 is still the most widely used version.
- ~80% of websites using PHP are still running the EOL version 7.x.
And so on. It’s estimated that this kind of technical debt would require $1.52T to fix, despite the fact that it costs as much as $2.41T per year in cybersecurity and operational failures.
The real issue here is that, ever since the pandemic, software supply chain attacks have been growing exponentially. By different estimates, between 60% and 90% of all companies worldwide were impacted by a software supply chain attack in 2023. Simply put, hackers are taking advantage of the fact that companies rarely update their software, and are very slow to roll out updates if/when they do.
I’ve discussed in a previous article, Best Practices: How To Update Your Codebase Without Breaking The Build why software vendors are reluctant to update their codebase, but it almost always comes down to opportunity cost:
- Time and resources spent fixing things after an update is time and resources not spent building out differentiating features/functionality that increase market share.
The root of the problem, though, is almost always dependency management, which is rarely treated as first class citizen in the world of open source software. Organizations typically have excellent visibility into the packages (i.e., top level dependencies) their application requires, but much less visibility the further down the dependency tree you go.
Consider JavaScript where a single package can have literally hundreds of dependencies, or Python, which can have dozens, including binary dependencies written in C, Fortran or Rust. The pain of manually tracking down all of these dependencies is a key reason why Software Composition Analysis (SCA) tools exist for software vendors, and Software Bill Of Materials (SBOMs) are an increasingly common customer requirement.
While SCA and SBOMs don’t provide equivalent functionality, they do make it much easier (on a per application basis) to identify:
- The complete dependency tree <- a key DevOps requirement
- A complete list of Common Vulnerabilities and Exposures (CVEs), as well as their severity rating <- a key Security requirement
- Licenses, including which dependencies feature multiple licenses <- a key Compliance requirement
- Datedness, or how often a dependency is updated <- a key IT requirement
Whenever a change is requested (for example to patch a CVE, add a package, update a dependency, etc), the request inevitably results in a cascade of changes across the dependency tree, forcing all stakeholders to re-examine and reach a consensus on those changes. This is typically done using the tried-and-true method of “passing around a spreadsheet.” As a result, even with SCA tools in place the change can take weeks to approve, let alone roll out due to all the broken code that needs to get fixed and redeployed.
Simply put, today’s dependency management process is acting like a drag on the software industry, slowing down innovation and revenue generation, while exposing customers to cyberattacks.
Continuous Code Refactoring & Automated Dependency Updates
The only way to solve the problem is to make dependency management a first class citizen in your software development process. But depending on how many programming languages your tech stack supports, your teams are probably cobbling together multiple package managers, environment managers, SCA tools and repositories in order to be able to import, secure, work with and monitor their dependencies. All this complexity makes managing dependencies something your developers are more likely to dread than appreciate.
The root of the problem is that your company is focused on selling your software solution, not managing the dependencies in your software supply chain. It is a necessary component of your business, but it’s tangential to your goals. And investing in software supply chain management is a difficult business case to make, because dependencies provide you no differentiation nor competitive advantage since they’re available to your competitors, as well.
As a result, most software vendors never spend the time and resources to create the kind of dependency management solution that would:
- Build all dependencies securely from vetted source code in a reproducible manner in order to eliminate software supply chain attack vectors.
- Continuously update the codebase to remediate vulnerabilities and eliminate outdated dependencies.
- Automate code refactoring to fix broken first-party code.
But this is exactly what the ActiveState Platform can do for your business: automate dependency updates while avoiding breaking changes so you no longer need to avoid updating your software dependencies.
The ActiveState Platform can easily be integrated with any software development process. Instead of downloading suspect packages (along with all their dependencies) from a public repository and then trying to figure out which bad actors you’ve just let into your enterprise, your project’s open source environment is securely built on demand in the cloud, and then pulled from wherever it’s needed: development or QA environments; CI/CD containers; production instances, etc.
Updates to not only packages/dependencies but also the programming language itself are automated. And if you link your GitHub repository to the ActiveState Platform along with your test suite, code fixes are generated in a branch for you to take as and when you see fit.
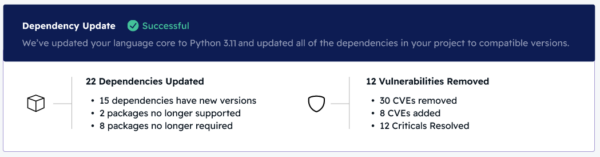
For example, automating a Python upgrade using the ActiveState Platform will generate an impact report, providing a summary of dependency changes (shown below), as well as a detailed dependency update assessment:
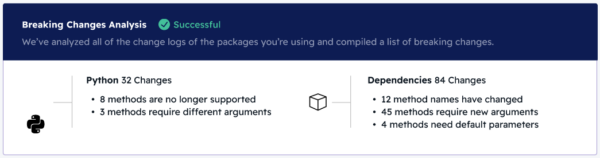
Similarly, the ActiveState Platform will also examine your code and generate a summary report (shown below) that’s indicative of the number of breaking changes that will need to be fixed:
A detailed report is also generated, which lists specific items to be updated, such as:
- Method names that may require updating
- Arguments that may be missing
- Modules that may be missing
- Variables that may need to be renamed
And so on. ActiveState relies on AI and our years of Python expertise to refactor your code and address all breaking changes. In this way, you can focus on delivering new features and functionality while our platform seamlessly keeps you up to date.
Conclusions – Automated Dependency Management
ActiveState’s “Get Current, Stay Current” initiative provides organizations with a simple way to dig themselves out from under the deluge of technical debt that accumulates in any successful enterprise by making dependency management a first class citizen.
You can take advantage of it to not only secure your organization’s software supply chain, but also reclaim the time and resources you might otherwise dedicate to updating your dependencies and refactoring your code.
Gone are the days of dedicating 10 to 20% of every sprint to maintenance work, which can suck up as much as 30% of your most experienced developers’ time. ActiveState’s regularly recommended updates, along with automated refactoring of your code, can save time for both your security and development teams.
Next Steps
Read about How To Outsource Software Supply Chain Maintenance and gain a significant competitive advantage over your slower-moving counterparts.