More Containers, More Problems
Containers have become foundational to modern software development. They power CI/CD pipelines, enable cloud-native architectures, and accelerate deployment cycles. But as container adoption reaches near universal scale, a troubling pattern has emerged: container adoption has outpaced container security.
Today, we’re excited to announce the release of our 2026 State of Vulnerability Management and Remediation Report: Container Security Edition. In this report we surveyed 250 DevSecOps leaders across North America to understand how organizations manage container security, where the biggest gaps exist, and what strategies teams are adopting to close them.
The findings reveal a stark disconnect between strategic intent and operational execution. While 100% of respondents told us that containerization was critical to their production strategy, 82% of them also admit that they’ve likely suffered at least one container-related security breach in the past 12 months. In short, containers represent a significant risk factor and attack vector. Organizations have good intentions to secure them, but they don’t always have the processes, tools, and best practices in place to efficiently remediate CVEs.
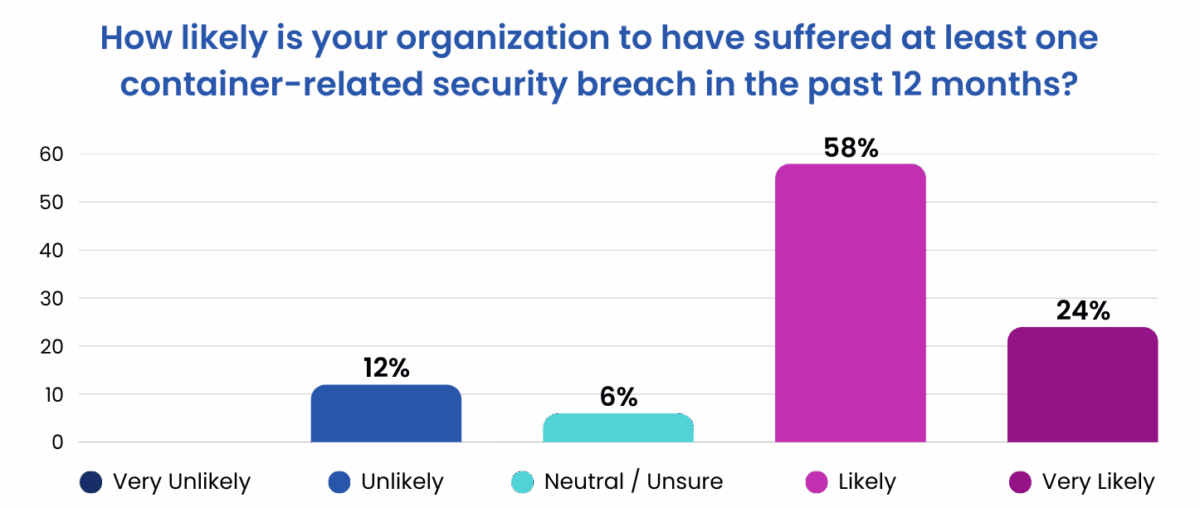
Visibility Gaps Create Hidden Attack Surfaces
Perhaps the most striking insight from the report is how visibility problems compound container security challenges. While 95% of DevSecOps respondents say container workloads account for half or more of their production footprint, 91% identify limited visibility into container components as their biggest security blind spot.
Teams Prioritize Convenience Over Security
Another key finding centers on trust versus practice. Although 77% of DevSecOps respondents trust curated catalogs of open-source and container images more than public registries, 90% still use lightly modified public images with little to no hardening. This gap exposes a fundamental challenge in container security: when platform engineering teams attempt to manually curate “golden images” these catalogs quickly become bottlenecks. Frustrated developers bypass the controls entirely, pulling packages directly from public registries and introducing unmonitored risk into production.
The Remediation Gap
Current approaches to container security have created what we call the remediation gap. Despite 98% of DevSecOps respondents ranking hardened container images as a high strategic priority, execution consistently falls short. The problem isn’t intent or investment momentum. The problem is that manual curation and the engineering challenges that come with it simply don’t scale.
AI and Automation Point to a Better Path
Despite these challenges, the report does reveal strong optimism about the future of container security. 100% of DevSecOps respondents are likely to use AI or automation to prioritize vulnerabilities, and 95% expect intelligent remediation to become standard practice by 2026. The appeal of AI-driven remediation is clear: rapid and targeted vulnerability response, operational consistency, improved accuracy, and significant reductions in both labor and business risk.
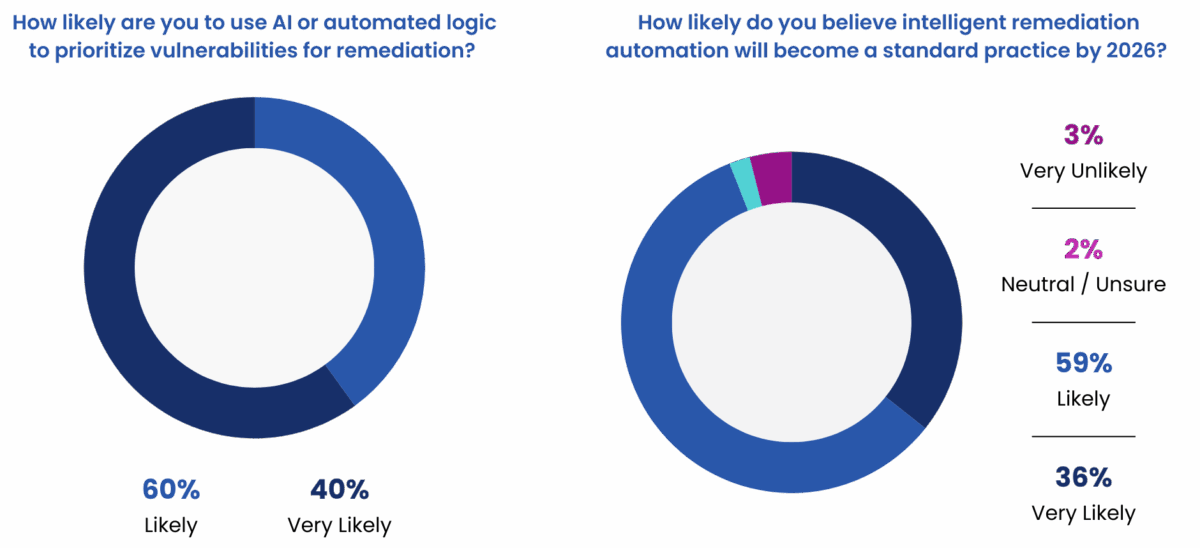
The Path Forward
Container adoption has outpaced security maturity across the industry. The good news is that DevSecOps leaders recognize the problem and are actively seeking solutions. The next 12 months will likely see widespread adoption of AI-driven remediation, policy-enforced runtimes, and curated container catalogs that eliminate the friction between speed and security.
For teams still relying on manual curation or lightly modified public images, the time to act is now. The risks are real, the costs are measurable, and the solutions are available. Container security doesn’t have to be a bottleneck. With the right tools and partners, it can become an enabler of both innovation and compliance.
The solution requires shifting from reactive scanning to proactive security. This means standardizing base image creation and approval workflows, partnering with providers who specialize in secure open source delivery, and implementing automated remediation pipelines that keep pace with the speed of modern development.
Read the Full Report
The ActiveState 2026 State of Vulnerability Management and Remediation Report delivers the complete picture of container security in 2026. Inside, you’ll find detailed data on container security trends, comprehensive analysis of AI-driven remediation strategies, and actionable best practices for closing the compliance gap in your organization.
Download the full report to discover:
- How leading organizations are addressing the visibility crisis in container security
- Specific strategies for moving from manual to automated remediation
- The role of AI in modern container security programs
- Practical steps for implementing custom container images that meet compliance requirements
- Industry benchmarks and data to help you assess your own security posture
Whether you’re a DevSecOps leader looking to reduce breach risk or an engineering manager trying to eliminate security bottlenecks, this report provides the insights you need to build a more secure container strategy.
Download the 2026 State of Vulnerability Management & Remediation Report









