Generate SBOMs. Enforce Compliance.
Move Fast.
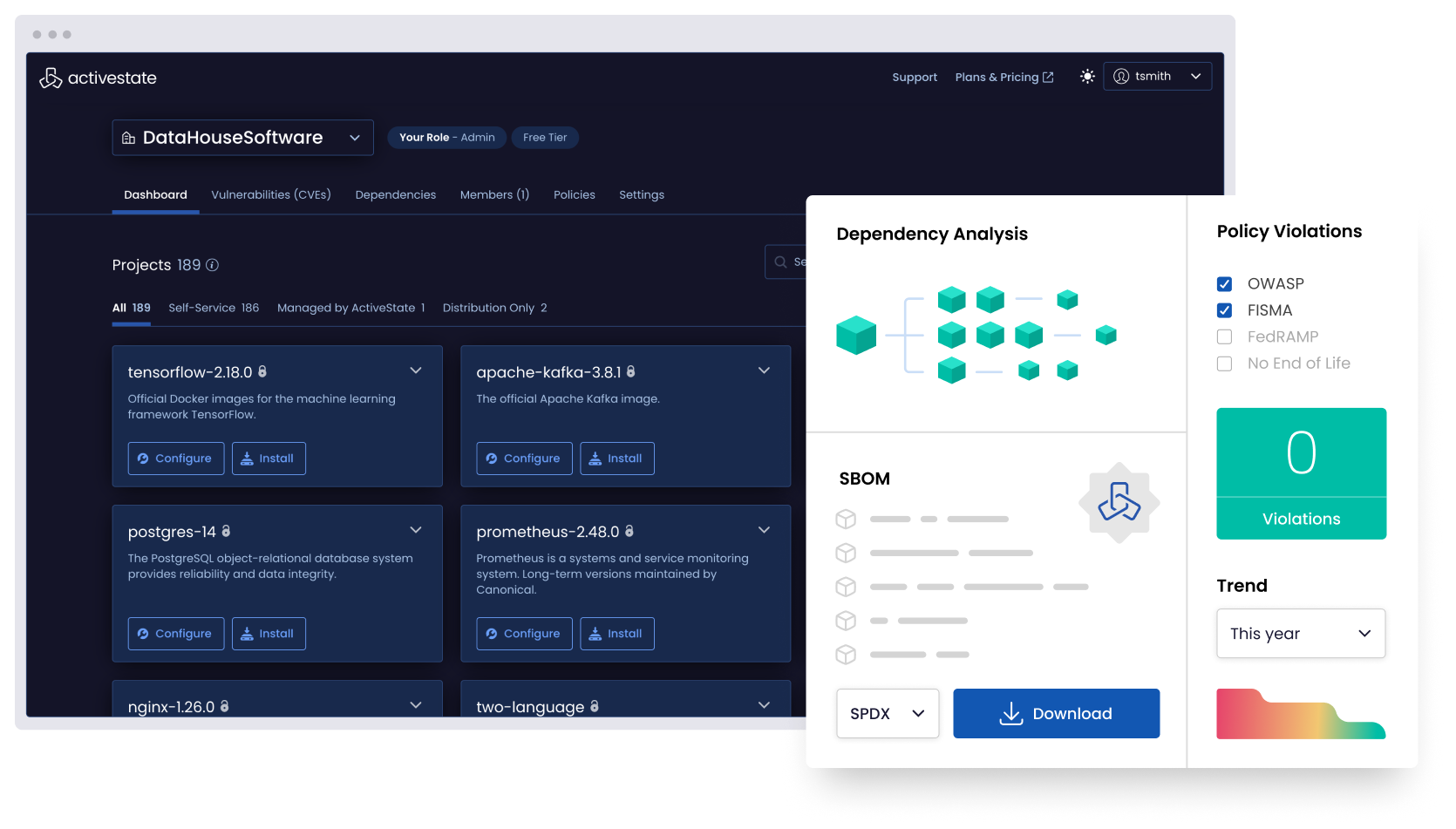







Prove your code is clean
Most SBOM solutions scan artifacts after the fact. The ActiveState platform builds them in from the start. This gives you a real-time audit trail and complete control over your open source usage.
- Generate SPDX and CycloneDX SBOMs automatically
- Trace every component back to its source
- Apply compliance policies by language, license, or team
“ActiveState is so transparent and makes our work seamless that sometimes we forget it’s there.”
– Ashish Saxena, Director of Engineering

Trace every component. Enforce every policy.
Build with traceability built in
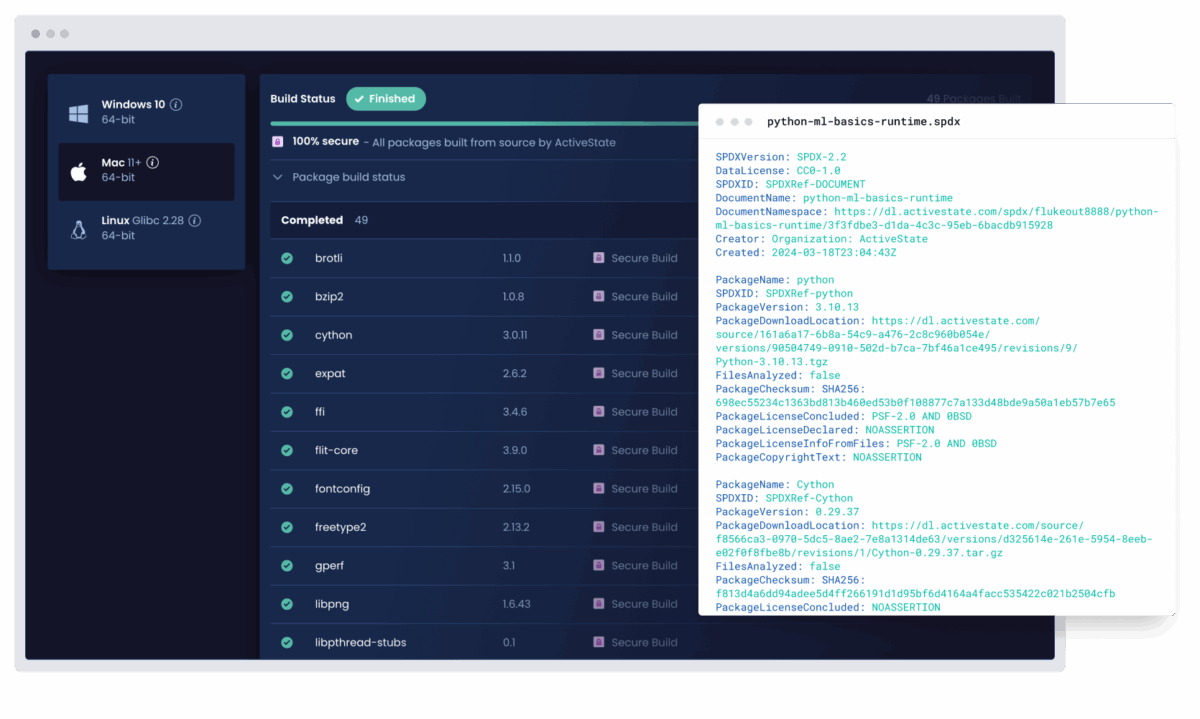
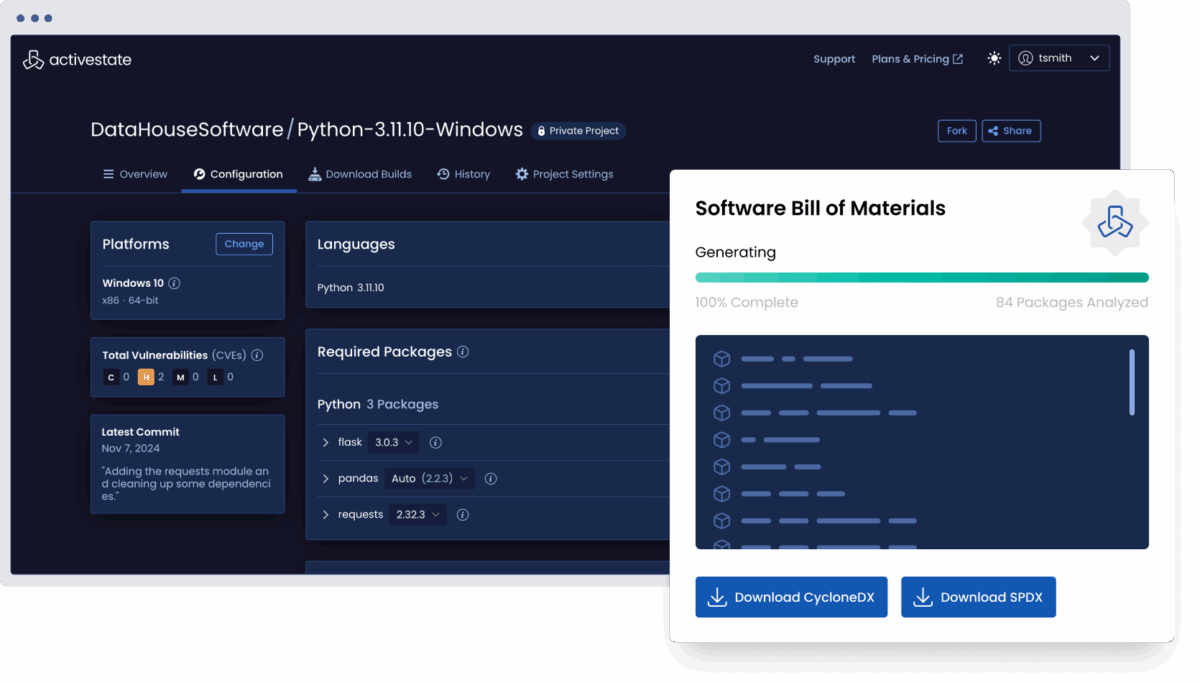
Automatically generate real SBOMs
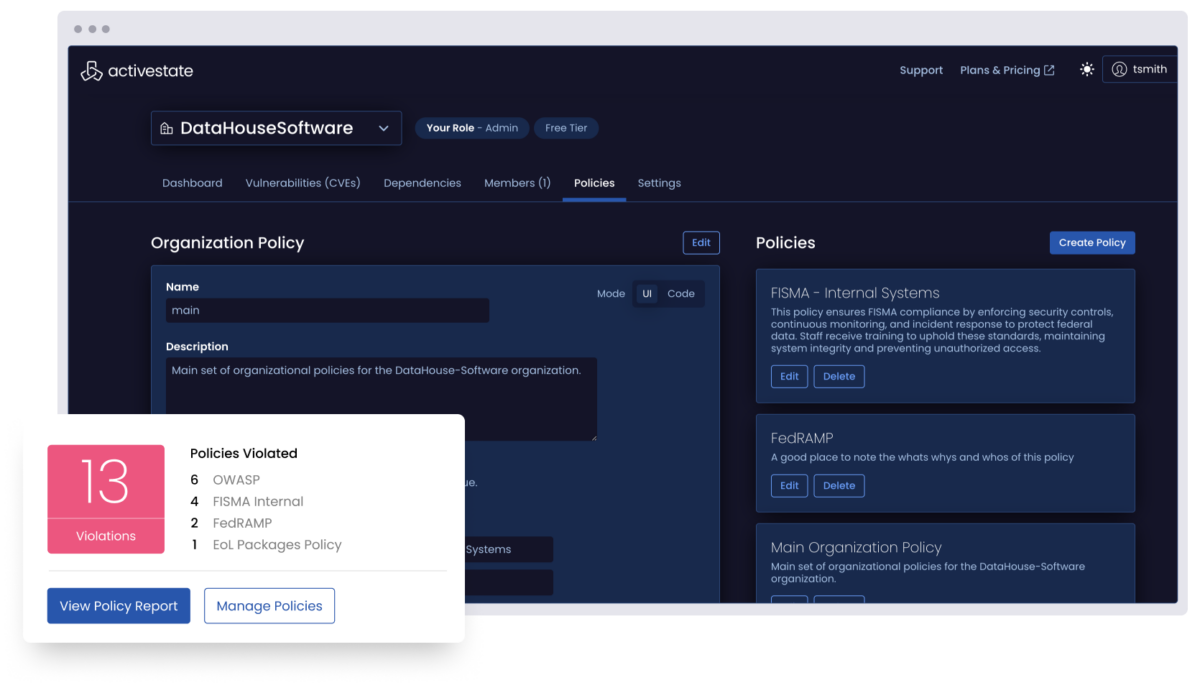
Apply and enforce compliance policies at scale
Enforce SOC 2, FedRAMP, and NIST 800-171 with every build. ActiveState’s SLSA3-compliant platform generates SBOMs, provenance attestations, and policy-enforced builds for every artifact.
From license restrictions to package versions, define and apply the rules that matter to your business across every build.
Experience the ActiveState platform in action
See how compliance becomes a natural outcome of how you build software.
In your demo, we’ll walk you through how to:
- Automatically generate SBOMs
- Enforce license and security policies across teams
- Maintain secure provenance and exportable audit trails with every build
- Automatically generate SBOMs
FAQs
What formats of SBOMs does ActiveState support?
You can automatically export SPDX and CycloneDX SBOMs—no CLI workarounds or extra tools required.
To learn more about how to create an SBOM with ActiveState or additional file format we support, check out our docs.
How is ActiveState different from other SBOM generators?
Most tools scan artifacts after the fact. ActiveState builds SBOMs in from the start, giving you real-time visibility, signed attestations, and verified provenance.
How does ActiveState ensure SBOM accuracy?
Every component is built from source and logged, ensuring your SBOMs reflect exactly what’s in your code.
Does the ActiveState platform help with SOC 2, FedRAMP, or NIST compliance?
Absolutely. Our SLSA3-compliant platform supports key standards with signed provenance, SBOMs, audit trails, and built-in policy enforcement.
Explore more resources

Regulatory Compliance & Open Source Software
Open source is rarely built with regulatory compliance in mind. Learn how to create & enforce compliance for OSS during software development.

How US Government ISVs Can Quickly Verify CISA Attestation
Software companies that sell to the US government face new hurdles when it comes to getting or keeping lucrative US government contracts: the need to verify CISA Attestation.

Modernizing & Securing Open Source Management in FedRAMP
Government agencies and contractors find it challenging to both meet requirements and introduce open source languages and libraries in software development workflows.



