The threat landscape is accelerating. With a constant barrage of newly discovered vulnerabilities and high-profile exploits like Log4Shell making headlines, enterprise organizations face immense pressure to respond faster and more effectively. Vulnerability remediation is no longer a reactive IT task; it’s a strategic capability that DevSecOps teams must master to protect their organizations, ensure compliance, and maintain business continuity.
This guide will walk you through what vulnerability remediation is, why it’s critical, the common challenges involved, a structured approach to the remediation process, the importance of automation, and best practices to optimize your strategy.
What is Vulnerability Remediation? Defining the Core of Vulnerability Management
Vulnerability remediation is the process of addressing and resolving security weaknesses within software components that could be exploited to compromise an application’s security, integrity, or availability. It’s a crucial phase within the broader vulnerability management lifecycle, which typically includes: discovery, assessment, prioritization, remediation, and validation.
Simply put, remediation is about fixing the underlying problem that created the vulnerability. For example, if a code injection flaw exists due to improper input validation, remediation involves updating the code to correctly validate and sanitize user input.
While observability focuses on gaining insights into your open source landscape and prioritization helps determine which vulnerabilities to tackle first, remediation is the action-oriented step that directly reduces risk.
The primary goals of vulnerability remediation are to reduce security risks, protect critical assets, and ensure compliance with relevant regulations. Organizations that neglect vulnerabilities in their software increase their risk of data breaches, denial-of-service attacks, and other operational disruptions.
Key Vulnerability Remediation Challenges for Modern Enterprises
DevSecOps teams often encounter significant hurdles when trying to implement effective vulnerability remediation, including:
• Volume and Velocity
The sheer number of vulnerabilities discovered daily, coupled with the rapid pace of software development, can overwhelm security teams with limited resources. The US National Vulnerability Database (NVD) has seen a tripling of Common Vulnerabilities and Exploits (CVEs) since 2016.
• Prioritization Difficulties
Not all vulnerabilities pose the same level of risk. Determining which vulnerabilities to address first can be challenging without proper context and prioritization frameworks. Many organizations treat all alerts with equal urgency, leading to wasted effort on less critical issues.
• Lack of Context on Application Implications
Understanding the potential impact of a vulnerability on a specific application and its business context is often not immediately clear. Generic risk scores like CVSS provide a baseline but don’t always reflect the real-world risk to your organization.
• Tool Sprawl and Lack of Interoperability
Organizations often utilize a variety of security tools (SAST, DAST, SCA) that operate in silos, leading to fragmented data and inefficient workflows. This lack of interoperability can hinder effective remediation efforts.
• Inaccurate Vulnerability Reports
Vulnerability scanners can generate false positives, identifying vulnerabilities that don’t actually exist, which wastes valuable time and resources on investigation. Conversely, incomplete scanning can miss critical vulnerabilities.
• Cross-Functional Silos
Friction between security, development, and operations teams can impede remediation efforts. Differing priorities and a lack of shared accountability can lead to delays in addressing vulnerabilities. Developers may perceive security as a bottleneck, while security teams might lack deep understanding of development environments.
• Lack of Remediation Guidance
Vulnerability alerts often provide limited or no specific instructions on how to fix the identified flaw, requiring significant effort from developers to determine the root cause and the appropriate remediation steps.
• Time-to-Remediate Challenges
Delays in ownership, unclear workflows, and manual processes contribute to long remediation times, increasing the window of exposure. Research suggests that the Mean Time To Resolution (MTTR) can range from 60 to 150 days, even though patches are often released within 9 days of discovery.
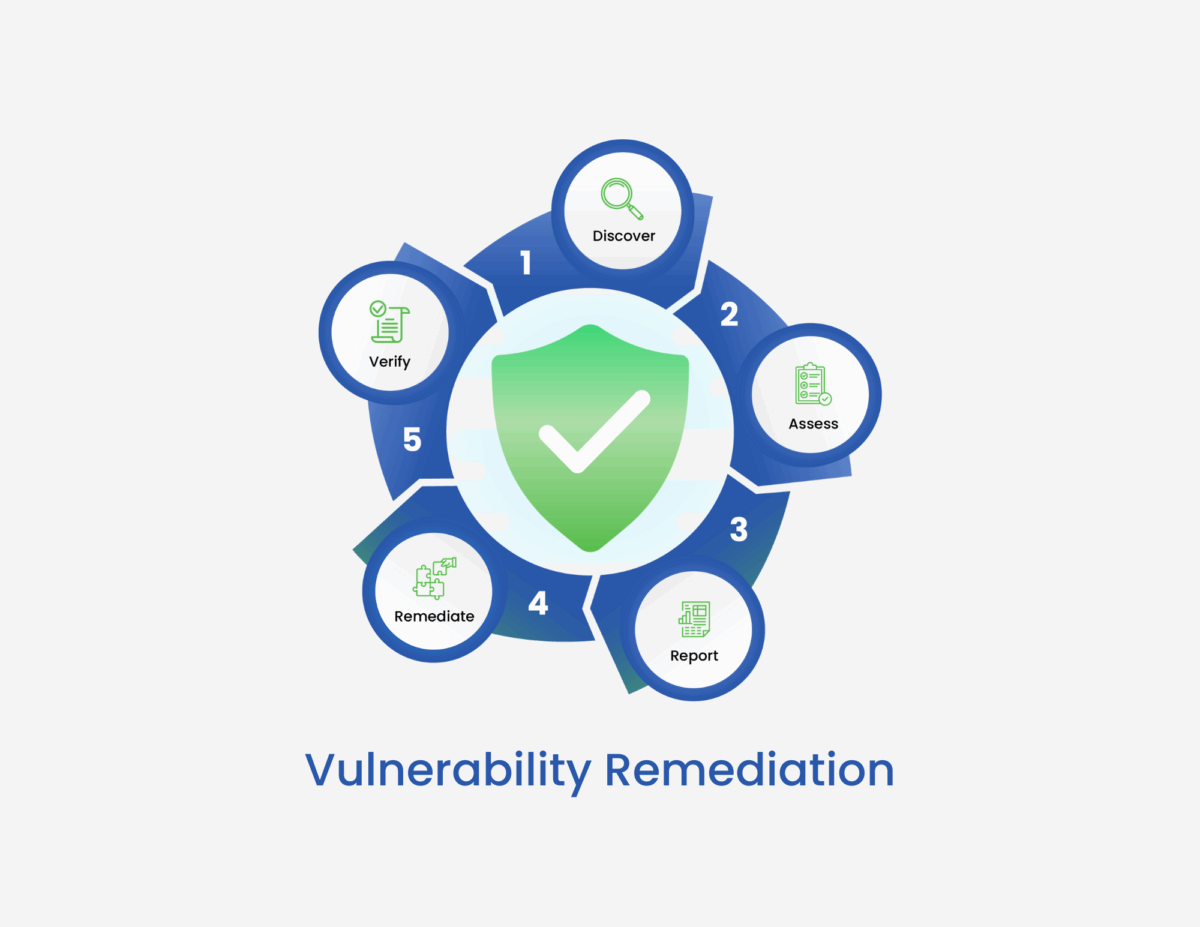
The Process of Vulnerability Remediation: A Step-by-Step Guide for DevSecOps
A structured and modern vulnerability remediation process is essential for effectively managing and mitigating risks:
1. Discovery & Analysis
DevSecOps professionals are empowered by discovery by providing broad observability across your open source landscape, identifying components and vulnerabilities to understand the Vulnerability Blast Radius, Proprietary Dependency Intelligence, Open Source Discovery, and Continuous Vulnerability Monitoring.
For analysis, ActiveState helps understand the potential impact with the Risk Prioritization Copilot, offering package scoring, vulnerability and license data, Update Impact Analysis, and Proactive Breaking Change Detection.
By ingesting the SBOMs created by your SCA and other scanning tools, ActiveState helps by providing comprehensive visibility into your open source landscape, including direct and transitive dependencies that might otherwise go unaccounted for.
2. Assessment
Once vulnerabilities are discovered, they need to be assessed to understand their potential impact and exposure within your specific environment.
This involves analyzing the vulnerability details, the affected components, and the context of their use in your applications. Vulnerability assessment tools, like Software Composition Analysis (SCA) scanners, can automate this process by identifying components and checking them against vulnerability databases.
3. Prioritization & Remediation Planning
Following vulnerability discovery and assessment, prioritization is crucial, and is based on factors like:
- Exploitability
- Asset criticality
- Business risk
- Threat intelligence
At this stage, organization-specific environmental metrics beyond basic CVSS scores are also taken into consideration.
Once prioritized, remediation planning involves defining ownership, establishing timelines, identifying dependencies, and selecting the appropriate fix, such as patching, upgrading, custom code, or configuration changes. ActiveState’s Risk Prioritization Copilot uses AI-powered analysis to help security operations teams focus on the most critical issues.
4. Execution
This is the stage where the actual remediation takes place. It might involve applying patches, upgrading to newer versions of libraries, implementing code changes, or adjusting configurations.
ActiveState’s Precision Remediation Pipeline automates component-level intervention by applying tested and permanent fixes, providing secure build generation from source, and offering extensible integration into existing CI/CD workflows. This includes adaptive patch forwarding, speculative builds for safe testing, and backporting for legacy systems.
5. Validation
After applying a fix, it’s essential to validate that the vulnerability has been successfully remediated and that no new issues have been introduced. This can involve re-scanning the affected systems, conducting penetration testing, and performing thorough testing.
6. Documentation and Reporting
Maintaining detailed records of the entire remediation process is crucial for auditability, compliance, and continuous improvement. This includes documenting the identified vulnerabilities, the remediation steps taken, the validation results, and any lessons learned.
What is a Vulnerability Assessment?
Vulnerability assessment is the process of identifying, quantifying, and prioritizing vulnerabilities within a codebase or system. These assessments can be automated using tools like Software Composition Analysis (SCA) scanners. SCA tools typically perform the following functions:
- Identify all components within a codebase
- Perform real-time vulnerability scanning by checking against online resources like the NVD
- Automatically notify codebase owners of new vulnerabilities while minimizing false positives
- Provide detailed vulnerability data, including threat intelligence, security risks, and severity levels to aid in prioritization
- Optionally suggest newer, secure versions of components
By automating vulnerability assessments, organizations can significantly reduce the Mean Time To Detection (MTTD) of vulnerabilities.
Automating Vulnerability Remediation: A Game-Changer for DevSecOps
Automating vulnerability remediation is critical for DevSecOps teams to manage the scale and speed of modern software development and the ever-increasing volume of vulnerabilities.
Automated remediation goes beyond simple patching and can involve:
- Policy-based actions for low-risk vulnerabilities
- Seamless integration with CI/CD pipelines to incorporate security checks and automated fixes early in the development lifecycle
- Automated deployment of tested and secure fixes
What are the benefits of automation?
- Increased Speed: Automating remediation tasks significantly reduces the time it takes to address vulnerabilities, minimizing the window of exposure.
- Improved Scalability: Automation allows teams to handle a larger volume of vulnerabilities without being constrained by manual effort.
- Enhanced Consistency: Automated processes ensure that remediation steps are applied consistently, reducing the risk of human error.
- Reduced Human Error: Automating repetitive tasks frees up security and development teams to focus on more complex and strategic initiatives.
It’s important to note that not every vulnerability is suitable for full automation. Legacy systems and high-risk applications might require more careful, manual intervention. DevSecOps teams should identify low-hanging fruit for automation, such as routine patches and vulnerabilities in non-production environments.
ActiveState’s platform offers features for automated component-level intervention and secure build generation, streamlining the automation of remediation processes.
Best Practices for Building a Mature Vulnerability Remediation Strategy
To build an effective and mature vulnerability remediation strategy, consider implementing the following best practices:
- Establish Remediation SLAs: Define Service Level Agreements (SLAs) for different risk levels to ensure timely remediation of critical vulnerabilities.
- Integrate Security into DevOps Pipelines (Shift Left): Incorporate security checks and automated remediation processes early in the software development lifecycle to catch and fix vulnerabilities before they reach production.
- Foster Shared Ownership: Promote collaboration and shared accountability for vulnerability management across security, IT, and development teams.
- Measure and Improve MTTR: Track key metrics like Mean Time To Resolution (MTTR) to identify bottlenecks and continuously improve your remediation processes.
- Regularly Audit and Test: Periodically review and test your remediation processes to ensure their effectiveness and identify areas for improvement.
- Create Remediation Playbooks: Develop standardized procedures and playbooks for addressing common types of vulnerabilities to streamline the remediation process.
- Leverage Threat Intelligence: Incorporate threat intelligence feeds to understand which vulnerabilities are being actively exploited in the wild and prioritize their remediation accordingly.
Conclusion: Take Control of Your Vulnerability Remediation Process
Effective and timely vulnerability remediation is no longer optional; it’s a fundamental requirement for modern enterprise cybersecurity. By understanding the challenges, implementing a structured process, embracing automation, and adopting best practices, DevSecOps teams can significantly reduce risk, improve compliance, and build more resilient applications.
Don’t let your teams drown in vulnerability alerts. It’s time to move beyond manual processes and embrace intelligent solutions that prioritize and automate remediation efforts.
Explore how ActiveState’s platform can help you streamline your vulnerability management lifecycle, enabling prioritized vulnerability management and faster remediation. What’s more, explore PRIORITIZE and ActiveState’s Risk Prioritization Copilot for intelligent vulnerability management.