The European Union Agency for CyberSecurity (ENISA) is an agency of the European Union (EU) that helps the EU address cybersecurity through policy and trusted solutions. Just as President Biden’s Executive Order has brought software supply chain security to the forefront of digital policy making in the US, ENISA has also recognized the growing threat, and predicts there will be a four-fold increase in supply chain attacks in 2021 over 2020.
ENISA defines a software supply chain attack as an attack on a software supplier that results in compromising one or more downstream customers, thereby allowing the originator of the attack (possibly months later) to gain access to the customers’ assets. Here, a supply chain includes both:
- The ecosystem of resources needed to design, manufacture and distribute a software product or service.
- The hardware, software, cloud and/or local storage on which the product/service is built and distributed.
The EU has been facing an increasing number of these kinds of attacks since 2020, causing widespread damage that has resulted in system downtime, monetary loss and reputational damage for many EU-based businesses.
Anatomy of Software Supply Chain Attacks
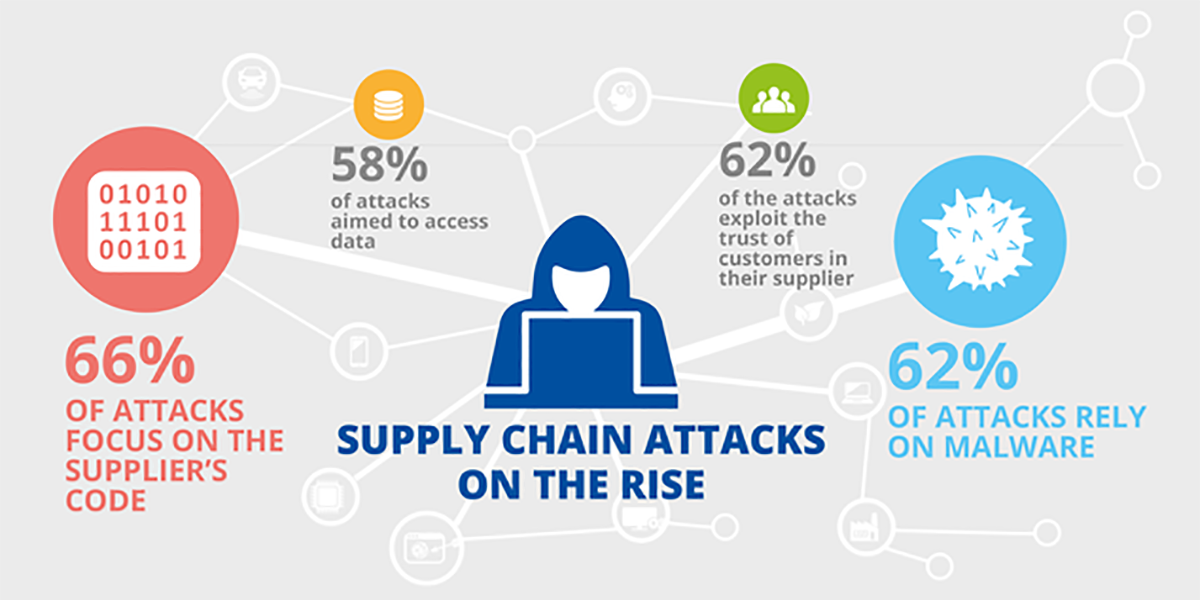
ENISA examined 24 supply chain attacks from January 2020 to early July 2021, and broadly found that:
- 66% of the incidents focused on the supplier
- In 62% of the cases, malware was the attack technique employed
- 58% of attacks were aimed at gaining access to data
- 16% of attacks were aimed at gaining access to people
The following table gives an indication of the types of attacks used to compromise specific assets of the software vendor. While the correlation of attacks to targets is not 1:1 (certain types of attacks were used against multiple assets), the table is instructive in showing the range of exploits bad actors are willing to use:
| Attack Techniques | Supplier Assets Targeted |
| Exploiting Software Vulnerability | Pre-existing Software |
| Open-Source Intelligence (OSINT) | Third-party Libraries |
| Malware Infection | Source Code |
| Exploiting Configuration Vulnerability | Configurations |
| Brute-Force Attack (password guessing) | Data |
| Social Engineering | People |
| Processes |
In general, the three most popular ways attackers are currently trying to undermine vendor’s software supply chain include:
- Hijacking of updates (as seen with the NotPetya attack)
- Undermining of code signing routines (as seen with the SolarWinds attack)
- Compromising open-source code before it’s imported into the organization
- For example, through typosquatting, which occurs when bad actors upload packages to public repositories that are named similar to popular packages.
By all accounts, the software vendor supply chain attacks ENISA has recorded to date are just the tip of the iceberg. The following visualization shows just how fast these kinds of attacks are accelerating, both in reach and rate:
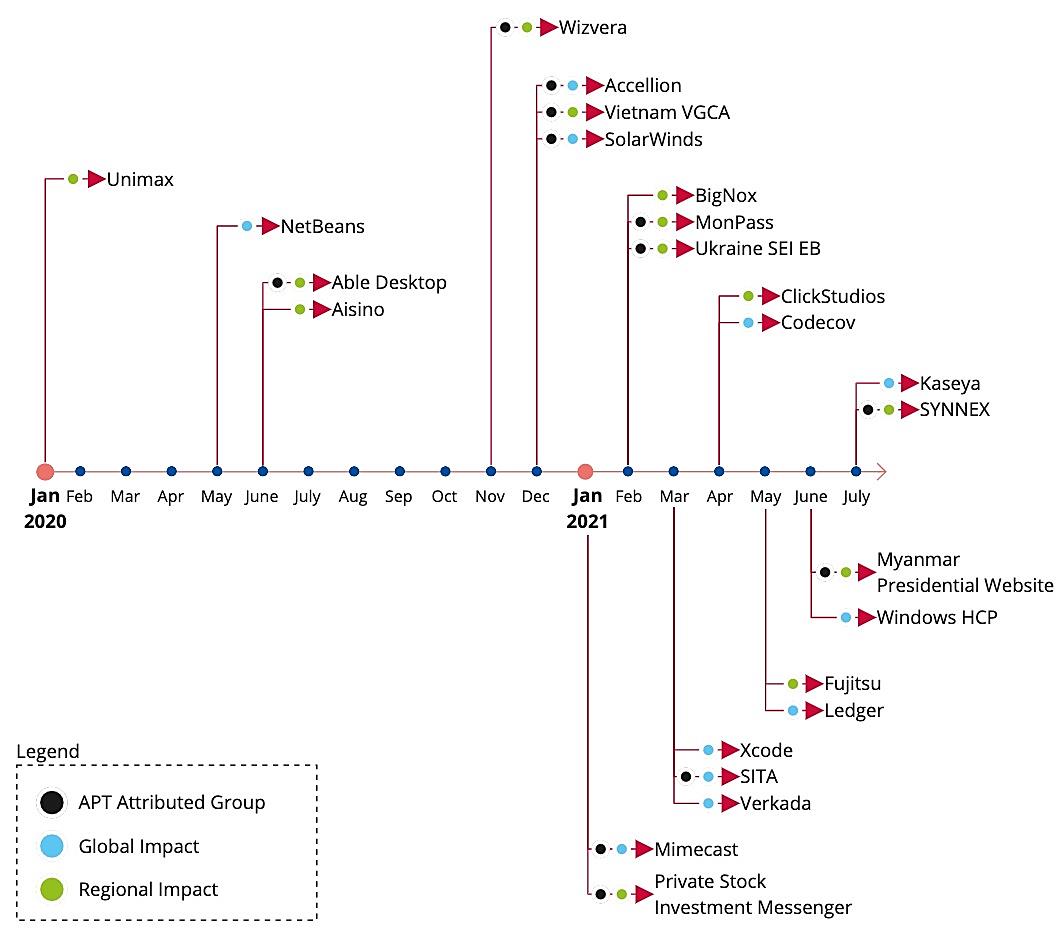
Source: ENISA Threat Landscape for Supply Chain Attacks
Addressing Software Vendor Weaknesses
One of the key findings from the ENISA report is that 66% of the time software vendors either did not know or else failed to report how they had been compromised. On the other hand, more than 91% of their customers knew exactly how they had been compromised. The result is striking: downstream organizations are FAR better prepared to detect and identify breaches than their software suppliers. The implication is that bad actors are targeting upstream suppliers because they are seen as poorly protected against cyberattacks compared to the customers they serve.
To address their supply chain security shortcomings, software vendors must (at a minimum):
- Ensure that the infrastructure and software development processes used to create and deliver products and services follows cybersecurity best practices.
- For example, MITRE D3FEND provides a framework in the form of a knowledge graph that maps cyberattacks to cybersecurity countermeasures.
- Provide customers with assurance that their infrastructure and processes conform to known standards.
- For example, ISO/IEC 27001, IEC 62443-4-1, IEC 62443-4-2, or CSA Cloud Controls Matrix for cloud services, etc.
- Provide customers with assurances that their development processes conform to know standards.
- For example, Google SLSA provides a set of controls that can help ensure the integrity and security of software code/components that are imported, built and consumed during the software development process.
- Be able to attest to the integrity and origin of open source software used.
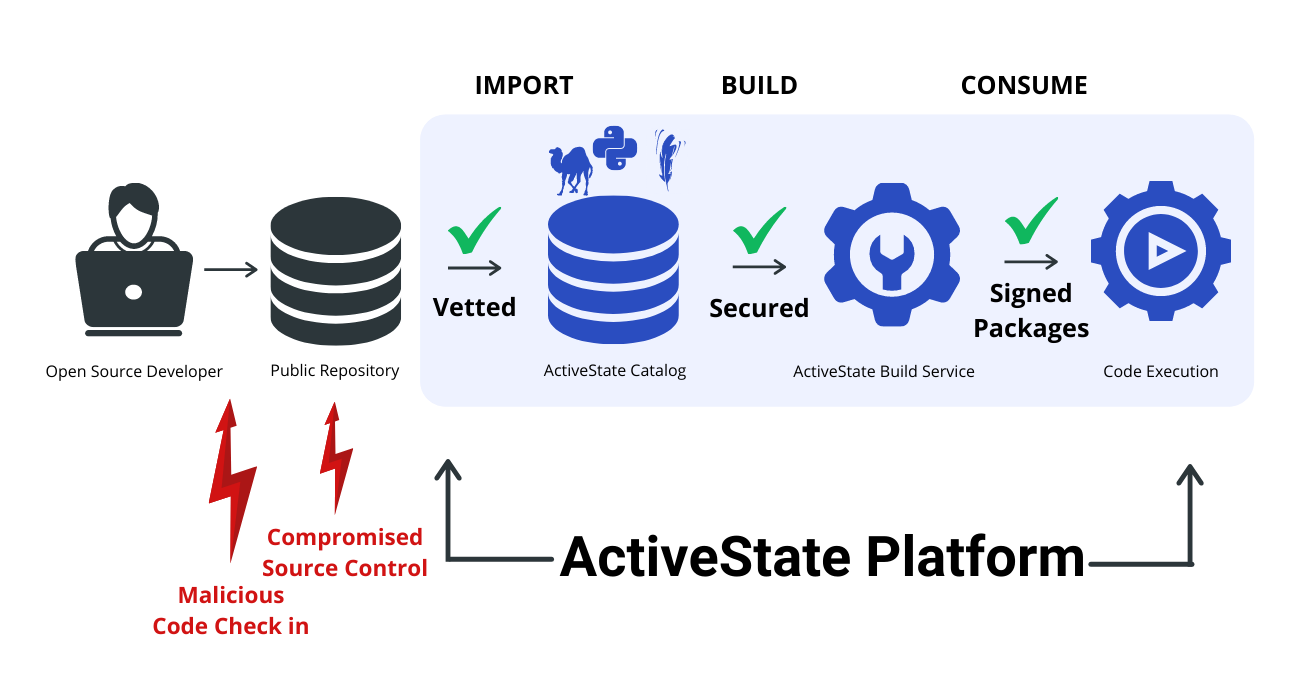
- For example, the ActiveState Platform provides verifiably reproducible builds of Python, Perl and Tcl, which, along with a provided Software Bill Of Materials (SBOM) allows you to attest to the provenance and integrity of the open source components you use in your software.
Conclusions: Software vendors must secure their software development infrastructure and processes
Supply chain attacks are a growing source of risk not only for software vendors, but for their customers, as well. Bad actors are leveraging the interconnectedness of global markets to be able to create maximum cybersecurity disruption from a single cyberattack. This shift has effectively made software vendors the front line of defense for the enterprise.
As shown by the ENISA study, software vendors need to take steps to better secure their software development infrastructure and processes, including:
- Implementing a strategy of continuous security for their supply chain, including active risk assessment and risk management.
- Implementing security and integrity best practices, such as those defined by MITRE D3FEND and Google SLSA.
- Seeking out vendors that can help them ensure the security and integrity of their systems and processes faster than a Do It Yourself (DIY) project.
The ActiveState Platform is a turnkey, end-to-end supply chain security solution that is quick to set up, easy to use and highly automated. You could spend years and millions of dollars integrating point solutions in order to protect your software supply chain in order to avoid becoming the next SolarWinds. We built the ActiveState Platform so you don’t have to.
Next steps:
- Watch our webinar on ‘Securing Your Python, Perl and Tcl Supply Chains’
- Sign up for a free account and try the ActiveState Platform for yourself
Recommended Reads
3 ways the ActiveState Platform can secure your open source supply chain







