Your All-in-One Vulnerability Management Platform
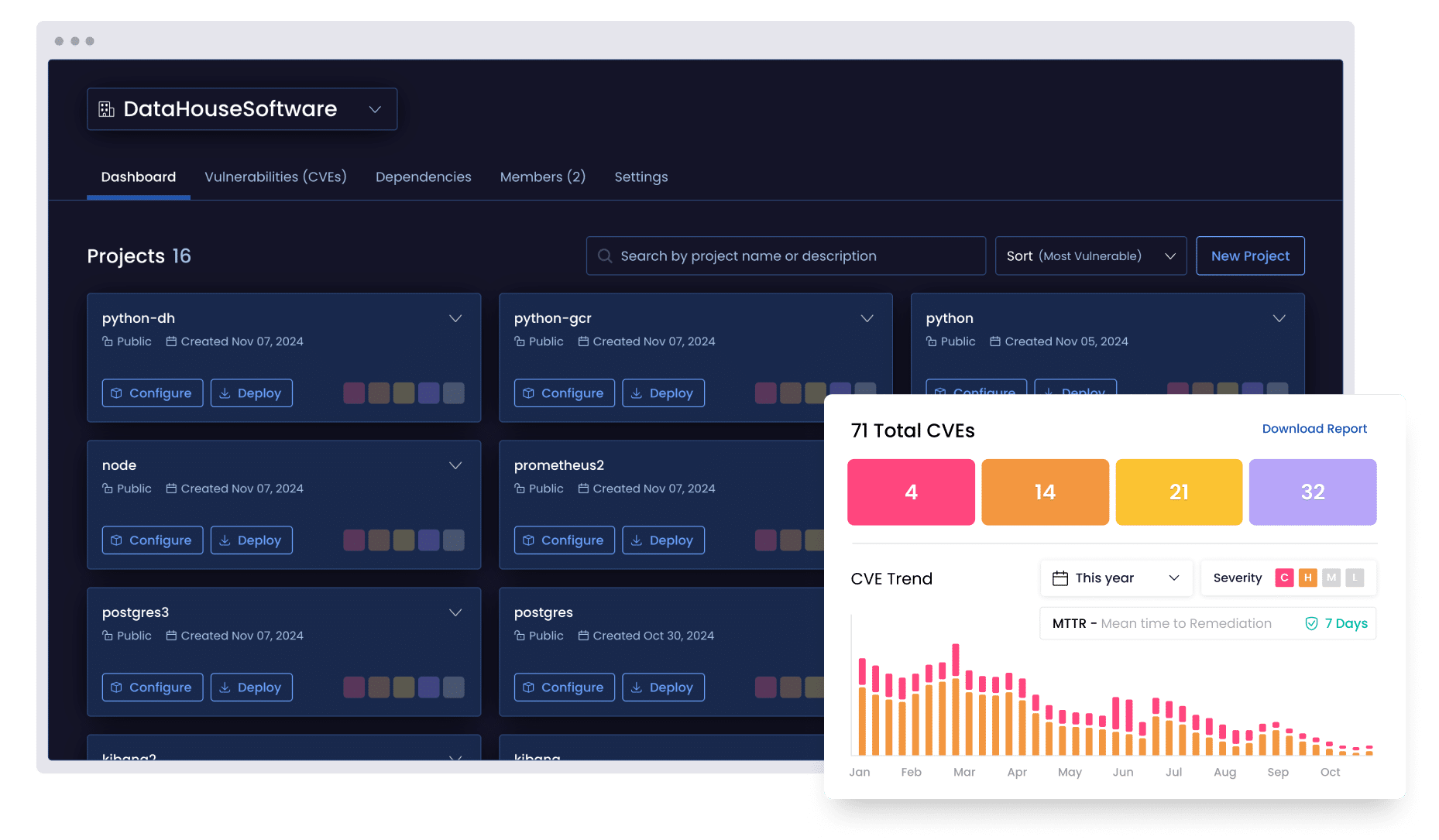







Track, triage, and remediate vulnerabilities with precision
Discover vulnerabilities at their root and understand their impact
Map the full scope of each vulnerability across your open source stack and reveal its root cause (and cascading impact) so your teams can prioritize and remediate with precision.
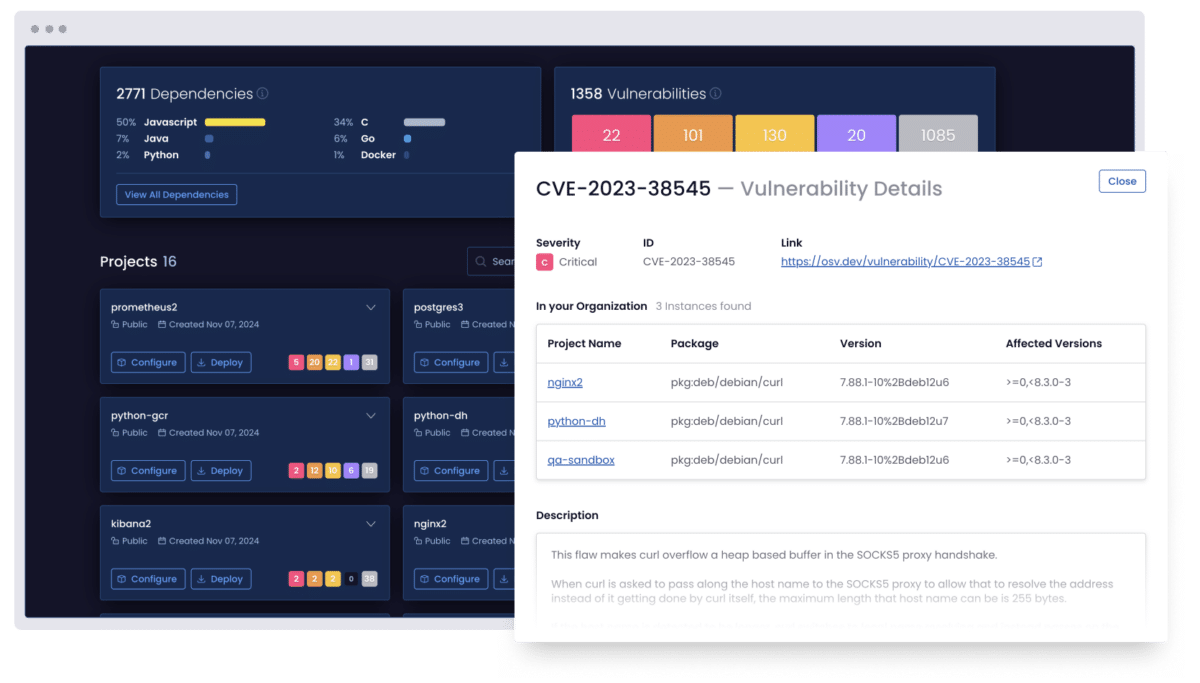
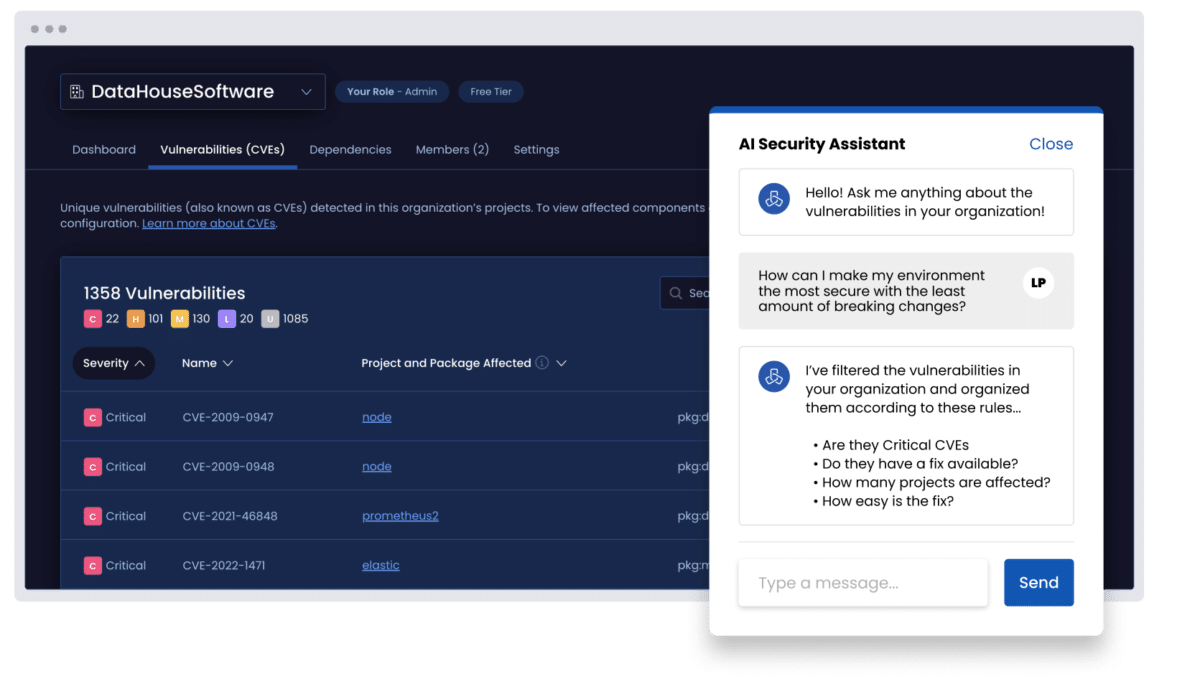
Prioritize vulnerabilities using AI and eliminate breaking changes
Use AI to analyze exploitability, breaking changes, and dependencies so teams can focus on remediating the vulnerabilities that matter most.
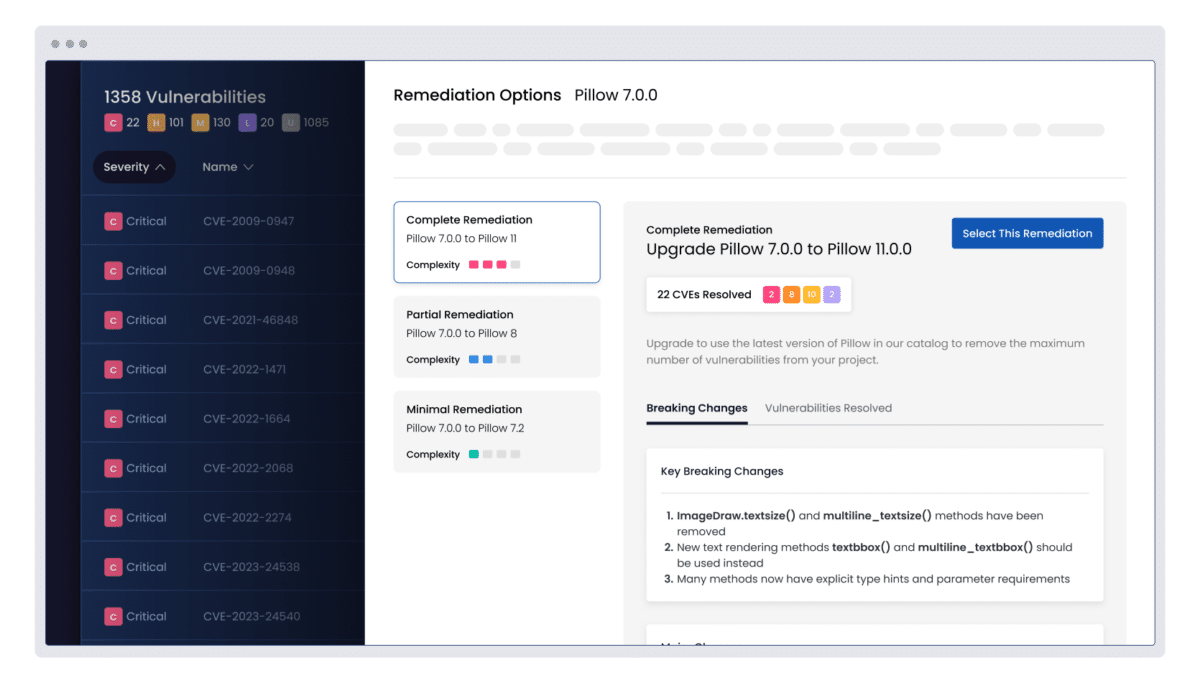
Remediate vulnerabilities automatically and apply secure fixes faster
Remediate open source vulnerabilities by applying tried and tested fixes, and build secure, tamper-proof components from source, all from directly within the ActiveState platform.

Building with Containers?
Platform features
Proprietary Dependency Intelligence
Organizational Impact Controls
Continuous Vulnerability Monitoring
Proactive Breaking Change Detection
Risk Remediation Workflow
Security Process Acceleration
Automated Component-level Intervention
Secure Build Generation
Extensible Integration
Integrate with the tools you already use
Seamlessly integrate with popular tools to secure your software supply chain.
Built for DevSecOps teams who don’t compromise on security or speed




One platform. Multiple languages. Fully managed.
ActiveState Python
Secure your entire Python ecosystem, not just ActiveState Python. The ActiveState platform helps you automate builds, manage dependencies, and maintain compliance across teams and environments.
ActiveState Go
From microservices to enterprise systems, Go projects thrive with consistency. ActiveState gives you a secure way to build, share, and govern all your Go environments across teams, pipelines, and deployments.
ActiveState Java
Bring control and clarity to all your Java, not just ActiveState Java. ActiveState lets you manage builds, dependencies, and compliance from within a single view, making it easier to keep your Java projects secure and aligned across your enterprise.
ActiveState R
R environments can be difficult to standardize regardless of where you are in the product lifecycle. ActiveState helps you build reproducible, secure R environments that meet compliance requirements and scale with your team.
ActiveState Perl
Managing Perl shouldn’t be a black box. ActiveState helps you modernize and maintain all your Perl applications with a secure, centralized approach that improves collaboration, versioning, and policy enforcement.
ActiveState Tcl
Tcl is powerful, but managing dependencies and environments at scale can get messy. ActiveState brings visibility and control to all your Tcl usage, ensuring builds are secure, compliant, and consistent across systems.
ActiveState Ruby
Simplify how you manage Ruby across your organization. ActiveState provides secure Ruby builds, streamlined dependency management, and compliance tooling so teams can focus on shipping code, not maintaining environments.
The ActiveState platform manages 40 million unique artifacts across multiple language ecosystems.
Get in touch to discover more supported languages.
FAQs
Does The ActiveState platform support on-prem, hybrid, and cloud environments?
Yes. The ActiveState platform is built to support all environments — including on-premise, hybrid and cloud environments — so you can integrate our platform and remediate vulnerabilities wherever your applications live.
How is the ActiveState platform different from traditional SCA tools?
Traditional SCA tools are reactive, only scanning for vulnerabilities after an application has been deployed. The ActiveState platform takes a preventative approach, and its vetted catalog of open source components helps block risky direct and transitive dependencies from entering your environment in the first place. It also digs deeper than most tools, analyzing down to the C library level to uncover issues others might miss.
Why is ActiveState’s catalog larger than others in the space?
The ActiveState platform gives you access to the world’s most comprehensive open source component catalog, featuring more than 40 million unique artifacts and nearly three decades of open source build expertise.
Our catalog is larger than everyone else’s because it pulls from a broader range of ecosystems and keeps an immutable, historical record of every package created, including legacy packages that disappear from the internet. Moreover, our catalog is always growing in response to user’s needs thanks to a sophisticated system that is constantly ingesting from these ecosystems.
This means better visibility, reproducibility, and more comprehensive vulnerability coverage.
Does the ActiveState platform use AI across its capabilities?
Yes. AI is used to generate insights such as breaking change reports, helping teams understand the risk and complexity of upgrades based on a vast knowledge base of packages and builds.
Does the ActiveState platform support legacy software?
Yes. The ActiveState platform has a deep catalog of legacy components and offers enterprise support for things like backporting security patches and end-of-life software, making it ideal for maintaining stability and security in older legacy environments.
Stay one step ahead of your open source vulnerabilities

Why VMaaS Is Important for Your Enterprise Cybersecurity Strategy
ActiveState’s VMaaS solution delivers the last mile of vulnerability management through risk prioritization, precision remediation, and expert guidance. Here’s why it’s important to your enterprise cybersecurity strategy.

The 2025 State of Vulnerability Management and Remediation Report
Open source powers everything. Our latest report provides a candid look into how organizations manage vulnerabilities and remediation, and why traditional tools are no longer enough to tackle vulnerability remediation.

What is VMaaS? Understanding Vulnerability Management as a Service
Does it feel like your DevSecOps teams are constantly dodging cybersecurity threats? It’s a frustrating reality for many. Explore why opting for security-as-a-service can help your team overcome these mounting challenges.
Experience the ActiveState platform in action
Fill in your details to book a demo with one of our product experts.
Here’s what to expect:
- A no-commitment product walkthrough
- Discussion built on your top priorities
- Your questions, answered