Cybersecurity professionals are increasingly stressed out as traditional email attachment, zero day exploit and fake URL attacks continue to escalate alongside new cybersecurity attacks originating in the software supply chain.
In some industries, attacks have grown by more than 20% in 2023 compared to 2022, even as ransomware payments hit a record $1.1B in 2023.
Source: Infosecurity Magazine
The result has been a crisis among cybersecurity professionals, reflected by increasing stress, cynicism and exhaustion. While budgets in many cases have been keeping pace with the growing threat, they have yet to translate into the establishment of a comfort zone. Attack vectors are simply evolving too quickly, driven in large part by the use of AI tools.
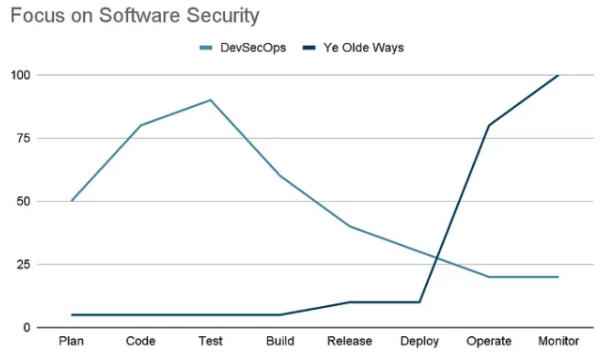
But many organizations are all too willing to shoot themselves in the foot, as well. For example, a recent GitLab DevSecOps survey shows that the shift left is far from smooth, with security personnel believing that application security is now a Dev responsibility, while Devs still think it’s primarily security’s responsibility:
Source: GitLab 2023 Global DevSecOps Report
While the DevSecOps value proposition of “shifting security left” is undeniable, most organizations struggle to reap the benefits. Traditionally, code is delivered much faster, but then the organization struggles with security alerts post-deployment. With DevSecOps, code is delivered much slower, but the strain on cybersecurity professionals post-deployment is greatly reduced:
Source: Shifting Security Down Early
Unfortunately, the industry as a whole continues to do what the industry has always done, hoping that (somehow) things will get better, namely triaging post-deployment. The result is an ever-growing number of alerts and crises that puts more pressure on cybersecurity professionals. Unsurprisingly, a number of recent surveys reflect this trend, including a Cyberark survey that found 59% of cybersecurity employees were simply worn out, even as there’s a growing shortfall of almost four million cybersecurity workers globally.
Without replacement workers, burnout only gets worse, leading to lax security as exhausted teams lose focus. The solution? While there is no silver bullet, you can take advantage of automated upstream tools to ensure fewer issues are being introduced in the first place. In other words, shift your focus from being reactive to being proactive instead.
Proactive CyberSecurity Tools
The practice of DevSecOps is a great way to get proactive about security, but few organizations are willing to trade off the slower delivery of code for the security gains it provides. One way to address the productivity loss is to use managed tools, instead.
Managed tools minimize the cognitive load on your dev team, allowing them to focus on the real value, typically closing competitive gaps or creating differentiating functionality. When that tool also addresses the kinds of security issues that overwhelm your cybersecurity teams, its benefits become exponentially valuable.
For example, a zero-config CI system for open source dependencies like the ActiveState Platform delivers:
- Dependencies (as well as entire runtime environments) built from vetted source code to ensure security.
- An automated SaaS build system that requires (next to) no time/resources to configure, maintain or manage.
As a result, organizations gain all the benefits of vendoring their dependencies, without the overhead of having to manage those dependencies themselves, including:
- Reduced threat of vulnerabilities, since there is no barrier to updating/patching dependencies (runtime dependencies conflicts are automatically solved, and the runtime rebuilt in minutes).
- Reduced threat of malware, since dependencies are built from vetted source code rather than imported as prebuilt binaries where hackers can more easily hide malicious code.
- Less false positives, since signed attestations and SBOMs are generated as verifiable artifacts to ensure the runtime has not been compromised prior to deployment.
By securing your software supply chain in this way, you can reduce the volume of alerts, warnings and incidents that result in burnout and lapses in security.
For example, the software supply chain attack on VOIP software vendor 3CX in 2023 resulted in more than 600,000 client systems being compromised. While it was the VOIP software installer that included a malware-infected open source package, the root cause of the incident was alert fatigue: analysts ignored alerts that they believed to be false positives.
Such incidents are exactly why cybersecurity professionals need to share the burden by shifting left. When they can do so without impacting Dev’s ability to deliver software in a timely manner, everyone wins.
Conclusions: How to Make Cybersecurity Less Reactive
Performing complex tasks in high-risk environments inevitably leads to stress, which manifests itself in increased employee cynicism, exhaustion and burnout. With less vigilance comes more mistakes, which becomes a self-reinforcing mantra of “We’re not good enough, no matter how hard we work.”
Poorly designed cybersecurity strategies simply serve to exacerbate the problem. Enough. It’s time to work smarter, not harder: the burden needs to be shifted.
Automated tools like the ActiveState Platform effectively allow you to outsource the management of your open source dependencies. And since the dependencies are built from vetted source code using a SLSA Level 3 build service, you can be assured that they haven’t been compromised prior to deployment, dramatically reducing the volume of false positives that overwhelm organizations, especially when they initially adopt a DevSecOps strategy.
Next Steps:
Watch our webinar Breaking Cybersecurity Bad Habits: A DevOps Perspective to understand how you can leverage the ActiveState Platform to reduce burnout in your organization.