2023 saw a dramatic rise in cybersecurity incidents accompanied by growing losses due to cyberattacks, such as ransomware:
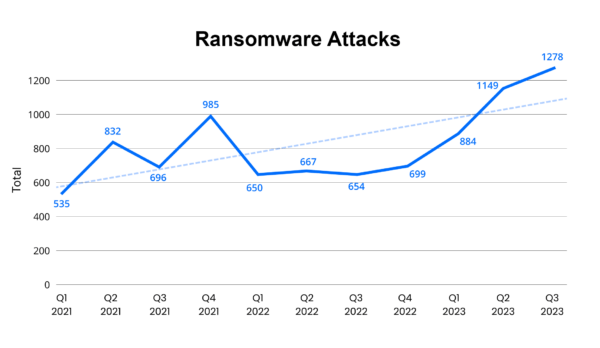
As the above chart from Corvus Insurance (which insures companies against the impacts of cybersecurity attacks) shows, global ransomware attacks are on the rise, with more ransomware attacks reported in the first nine months of 2023 than all of 2022. In fact, cybercrime has grown 15% year on year since 2015, and is estimated will cost companies $10.5 trillion annually by 2025, up from $3 trillion in 2015.
One of the key factors driving this growth is the transformation of ransomware attacks from being characterized as “disabling a target company’s digital infrastructure” to now exfiltrating sensitive information which the criminals threaten to leak on the dark web unless a ransom is paid. Some ransomware attacks have included both threats, effectively providing criminals with a double payday.
This new vector has been driven by hackers exploiting the software supply chain via malware:
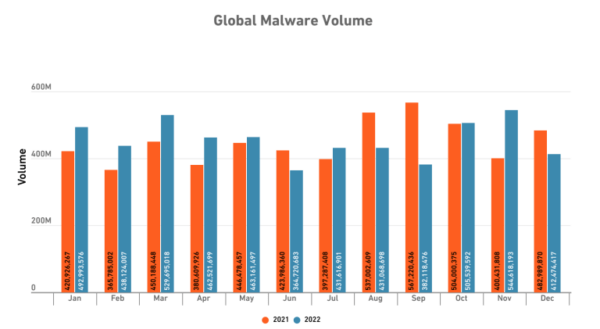
Source: Techopedia Cybersecurity Statistics
Malware is intrusive software intentionally created by hackers with the goal of stealing data and compromising applications/systems. Examples of common types of malware regularly found in open source ecosystems include trojans, spyware and, more and more commonly, ransomware.
As software supply chains become increasingly interconnected, vulnerabilities in one vendor’s code can expose a software developer’s application to attack. Hackers are increasingly exploiting this vector of attack, with the result that 40% of cyberattacks now occur indirectly through the supply chain.
Some of the key malware initiatives executed in 2023 included credential stealing malware, which may provide hackers with direct access to systems, or else insight into gaining access by using credentials to capture authorization tokens, cookies or else compromise Multi Factor Authentication (MFA).
“When 900 companies were asked what they thought were the most likely types of cyber attacks on their business, 60% responded with supply chain attacks.”
With SEC cybersecurity disclosure rules now in effect as of December 2023, public companies need to start taking the cybersecurity stance of their software supply chain more seriously. Designed as an aid to investors, the rules mandate that public companies must:
- Disclose material cybersecurity incidents within four business days of becoming aware of the attack.
- Annually disclose their cybersecurity risk management, strategy and governance.
But these rules also impact all suppliers of software to public companies, as well, since the software supply chain is only as secure as the weakest link in the chain. In fact, by 2025, it is estimated that 60% of enterprises will use cybersecurity risk as a key factor when determining their use of third-party software.
All this comes at a time when cyber security leaders are burnt out, frazzled from being constantly in a defensive posture as cyberattacks reach unprecedented levels and are being launched from more vectors than ever before. The state of being “always on” monitoring and responding to situations has driven many leaders to start looking at alternative, asynchronous solutions like SBOMs:
Source: BlueVoyant
While SBOMs offer a way to create a central repository of all software components deployed across an organization, they’re inherently static documents in a fast-moving landscape. What if there was a way to visualize where vulnerabilities are deployed across the extended enterprise that was always up to date but didn’t require constant monitoring?
Know Where Vulnerabilities are Deployed
Tradition has it that robust cybersecurity is the result of constant monitoring and efficient response. Without constant surveillance of the entirety of the organization’s digital ecosystems, threat levels escalate and their risk profile quickly becomes untenable.
Obviously, trying to improve cyber resilience and stay one step ahead of potential threats is a never ending challenge. Especially in the face of the fact that less than half of cybersecurity professionals claim to have high (35%) or complete visibility (11%) of vulnerabilities. At best, only around half of all organizations (51%) can claim to have moderate visibility into their vulnerabilities.
While most enterprises have at least one tool deployed that helps monitor and alert stakeholders when open source vulnerabilities are found, knowing where those vulnerable components are deployed remains a significant challenge.
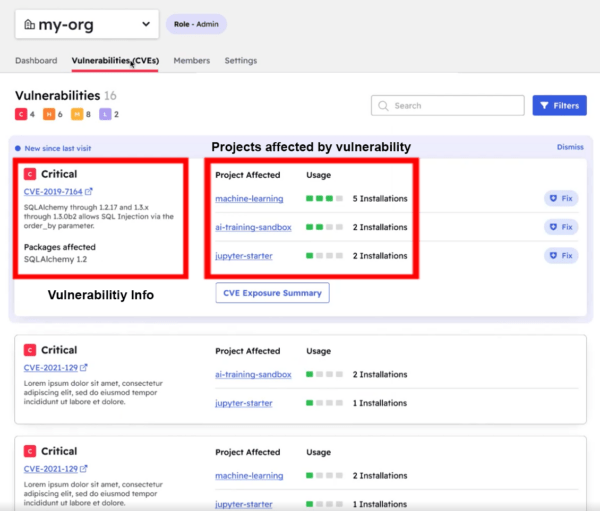
It’s for this reason that ActiveState has updated our Critical Vulnerabilities and Exposures (CVE) Dashboard to include the location of where vulnerable components are deployed, and by who. ActiveState’s CVE Dashboard provides:
- A complete list of open source dependencies in use across the organization, including all transitive dependencies, shared libraries and OS-native binaries.
- Where each set of dependencies is deployed across the extended enterprise.
- Who owns each project
For example, the following screenshot shows vulnerabilities by project:
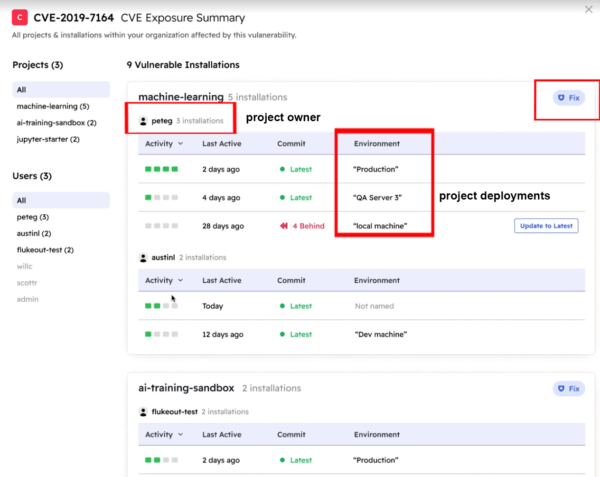
Clicking on the CVE Exposure Summary button shows you not only the environments in which those projects are deployed, but also the owner of those deployments, as well, down to the developer desktop environments on which the vulnerability exists:
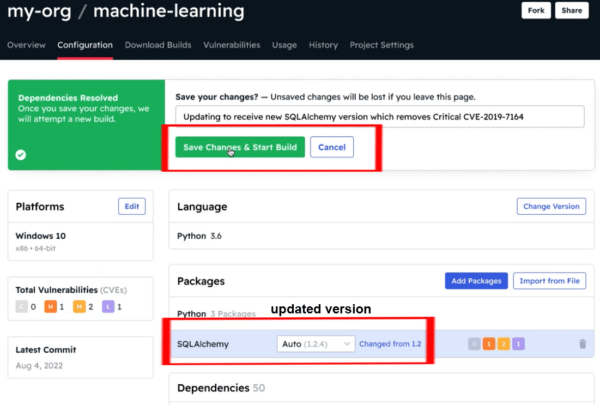
Finally, clicking the Fix button will take you to the ActiveState project itself, and automatically update the affected dependency to a newer version that fixes the vulnerability and is compatible with the rest of the runtime environment.
Clicking Save Changes & Start Build will automatically rebuild the runtime environment, ready to be tested and redeployed:
In this way, you can:
- Identify critical vulnerabilities as they happen
- Instantly identify the projects across your extended enterprise that contain the vulnerable component
- Instantly identify the owner of the vulnerable project(s)
And even help to fix the project, if required.
Next Steps
Watch the webinar Open Source Observability: Breaking Down Security Silos to see the CVE Dashboard in action.