Blog
All Blog Posts
Modernizing & Securing Open Source Management in FedRAMP and GovCloud Environments with ActiveState
Government agencies and contractors find it challenging to both meet requirements and introduce open source languages and libraries in software development workflows. Even using FedRAMP-authorized ...
Read More
Automate Your Governance and Policy Management with ActiveState
In today’s modern software development landscape, where speed to production and innovation reign supreme, open source governance and policy management is more important than ever. ...
Read More
Holiday Cheer and Code Confidence: DevSecOps Peace of Mind
The holidays are upon us, a time for reflection, celebration, and perhaps, a touch of… dread. Dread, you ask? For many DevSecOps teams, the holiday ...
Read More
4 Reasons Why Discoverability & Observability Matter for Enterprise Open Source
Open source software has become a cornerstone of enterprise development, with open source code making up 90% of components in modern software applications. Open source’s ...
Read More
Integrating Open Source Software At Scale: A Blessing or a Curse? You Decide
Open Source Software (OSS) has become the standard in enterprise software development. For most organizations, identifying all the OSS deployed for use internally, externally, and ...
Read More
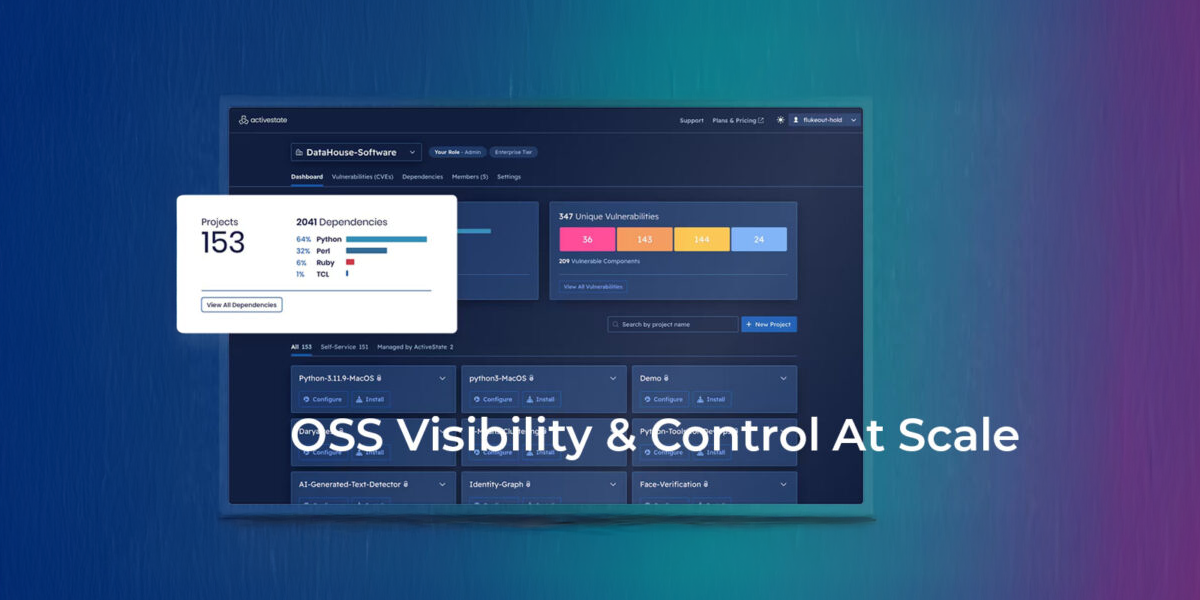
ActiveState Introduces its Open Source Management Platform to Secure the Software Supply Chain
ActiveState introduces unparalleled OSS visibility & control so you simplify your tool stack, reduce risk & accelerate development efforts.
Read More
Automating Vulnerability Management
Automating vul'n remediation is still limited by code coverage & breaking changes, but ActiveState closes some gaps to remediating at scale.
Read More
Regulatory Compliance & Open Source Software
Open source is rarely built with regulatory compliance in mind. Learn how to create & enforce compliance for OSS during software development.
Read More
The Cost Benefits Of Secure Reproducible Environments
Reproducible environments start with reproducible builds. Without it you get inconsistent environments, configuration drift & increased costs.
Read More
Open Source Discoverability & Observability
Identifying all the open source components your organization builds, deploys & makes use of is never straightforward. Learn how to it can be.
Read More
Software Supply Chain Security Enters the Trough of Disillusionment
Software Supply Chain Security helps with vulnerability management, but unrealistic expectations persist. Learn the greater benefits of SSCS.
Read More
Unlocking $8.8T of Secure Open Source Software
To take advantage of $8.8T of OSS effectively requires putting in place governance: the policies & processes that help manage & control risks.
Read More