The Weakest Link in the Software Supply Chain
The supply chain of most software vendors is extremely complex, spanning both public and private code repositories, open-source tooling, point solutions from multiple vendors, and more. Your supply chain is only as secure as its weakest link.
Recent attacks on SolarWinds and Codecov show that the build service is a key weak link that bad actors target.
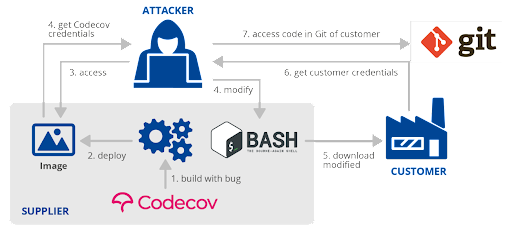 Image sourced from ENISA Threat Landscape
Image sourced from ENISA Threat Landscape
Securing the Build Service
Supply chain security starts with ensuring the security and integrity of the code you import. For example, in the case of open source components, best practices advocate importing only source code rather than prebuilt packages, especially if those prebuilt packages have not been signed by a trusted vendor.
- Secure Build Service – ActiveState’s build service is dedicated and runs on locked-down resources, minimizing the attack surface.
- Scripted Builds – Build scripts cannot be modified within the build service, preventing exploits.
- Ephemeral, Isolated Build Steps – Each build step executes in a separate container, which is discarded after completion.
- Hermetic Environments – Containers lack internet access, preventing remote resources from being included dynamically.
ActiveState Platform: Turnkey Supply Chain Security
The ActiveState Platform provides software vendors a turnkey, supply chain security service that’s quick to implement, easy to use, and highly automated.
Try the ActiveState Platform by signing up for a free account at platform.activestate.com
About ActiveState
ActiveState is a trusted choice for developers seeking secure open-source language solutions.
How to try the ActiveState Platform for your Python, Perl, and Tcl projects?
Developers can sign up for our Platform and use it to build a runtime environment.