Prevent Supply Chain Attacks from the Inside Out
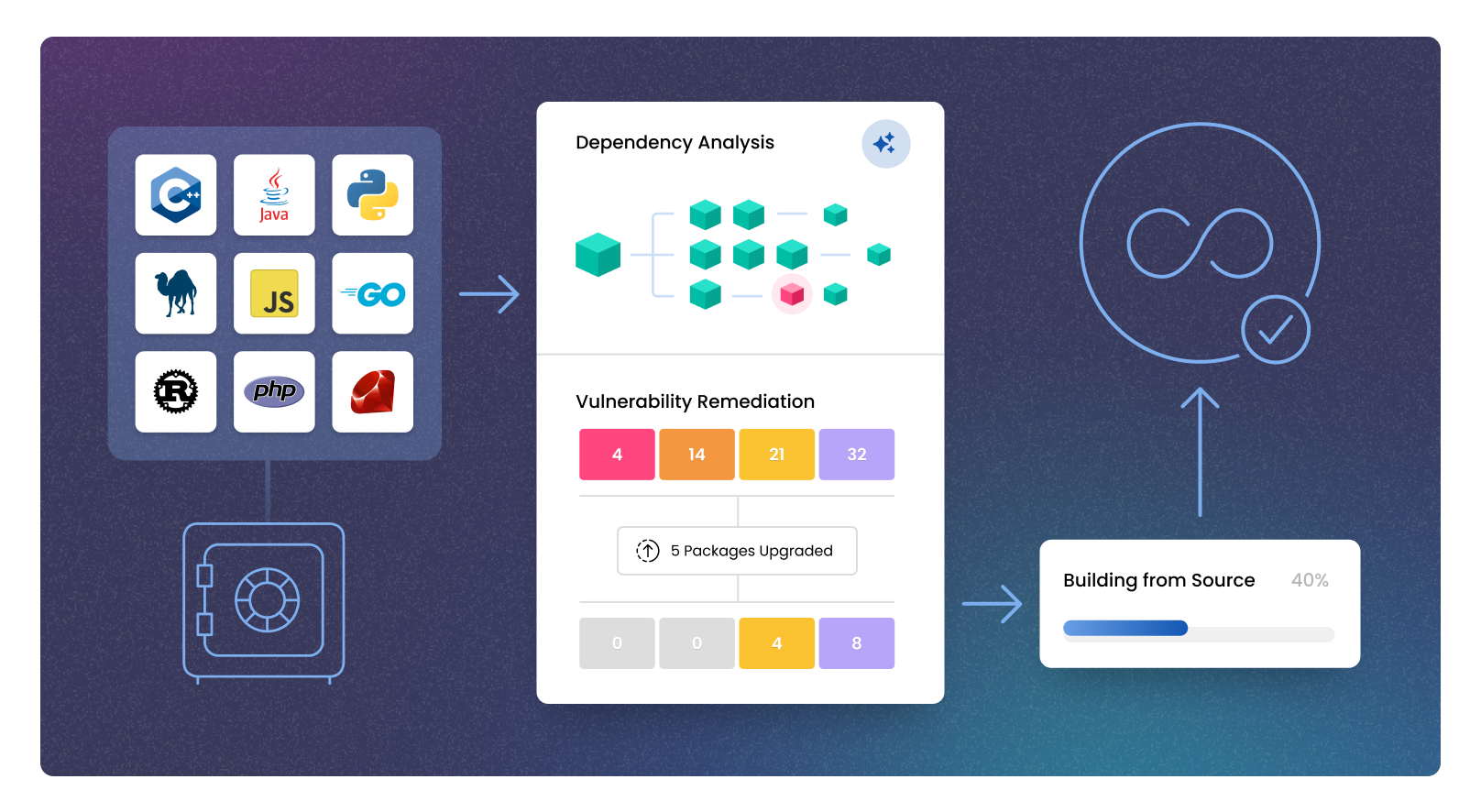







Shift left without losing control
Your developers need speed. Your security team needs oversight. ActiveState makes both possible by embedding security into the earliest stages of development.
- Detect vulnerabilities across transitive dependencies
- Eliminate tampering with secure build generation
- Generate SBOMs and apply policy enforcement automatically
“I don’t have to think too much about security and the complications anymore because ActiveState does it for me.”
– Stacy Leon, Sr. Technical Specialist
Secure by design. Compliant by default.
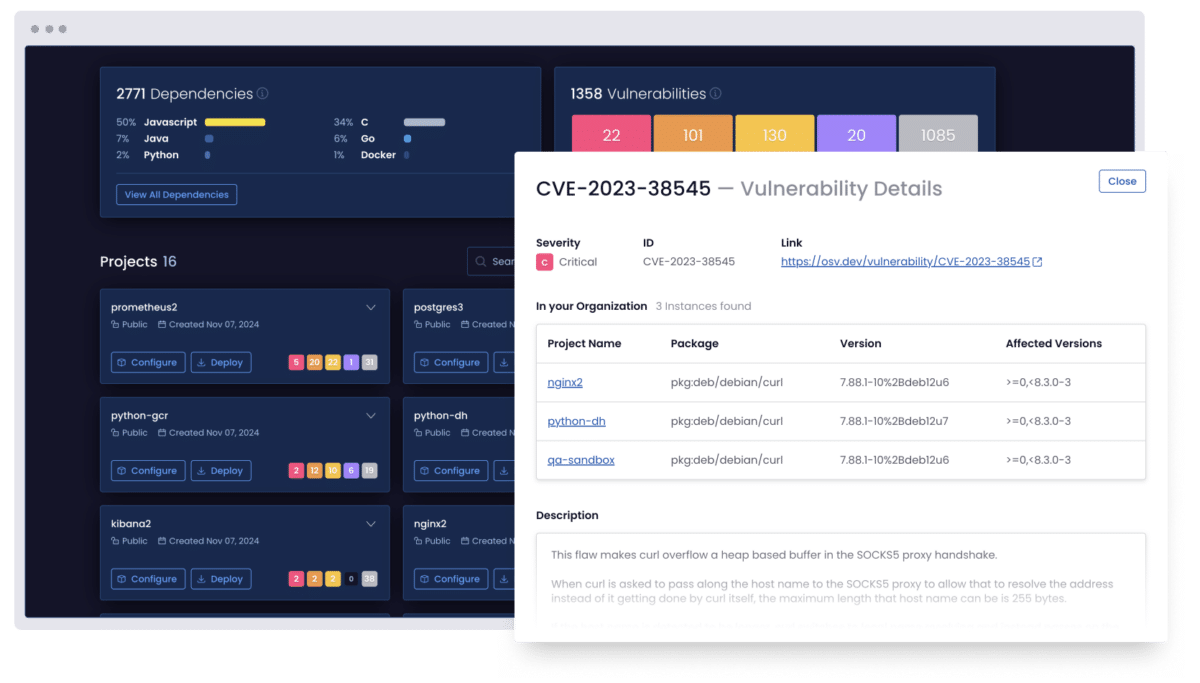
Scan your software supply chain dependencies
Uncover known vulnerabilities across your code, third-party packages, and even transitive dependencies.
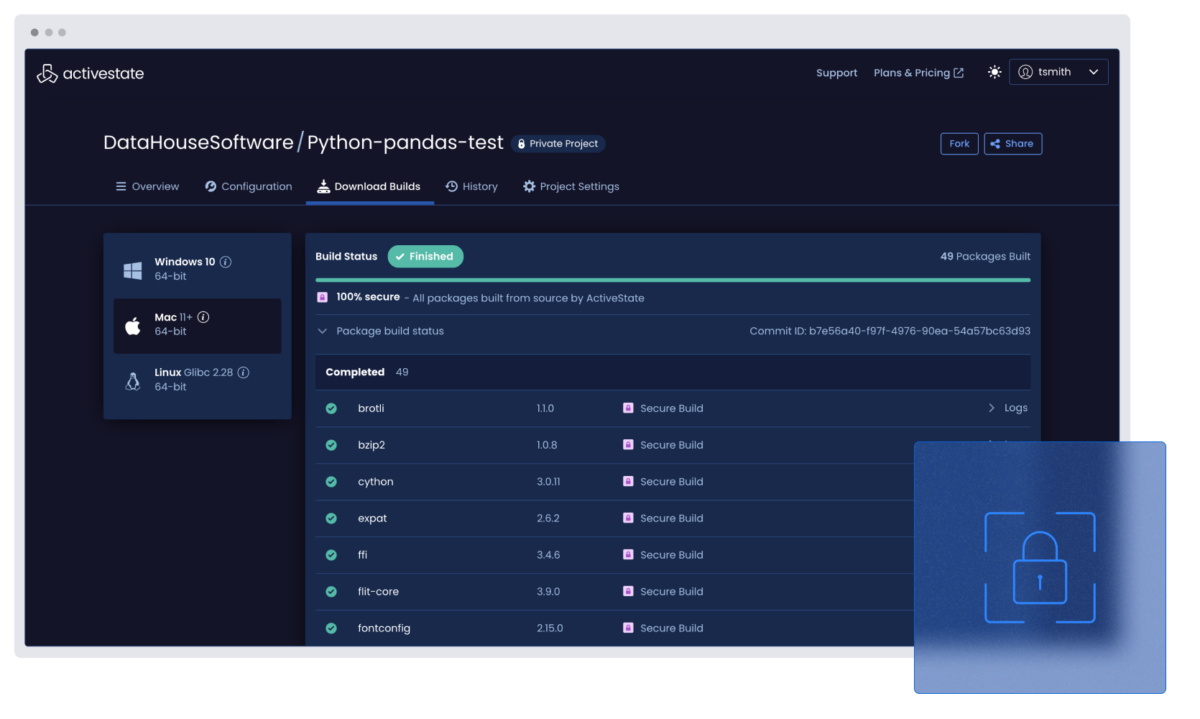
Lock down your builds with reproducible pipelines
Secure every component with verifiable, build-from-source processes. No tampering. No mystery artifacts.
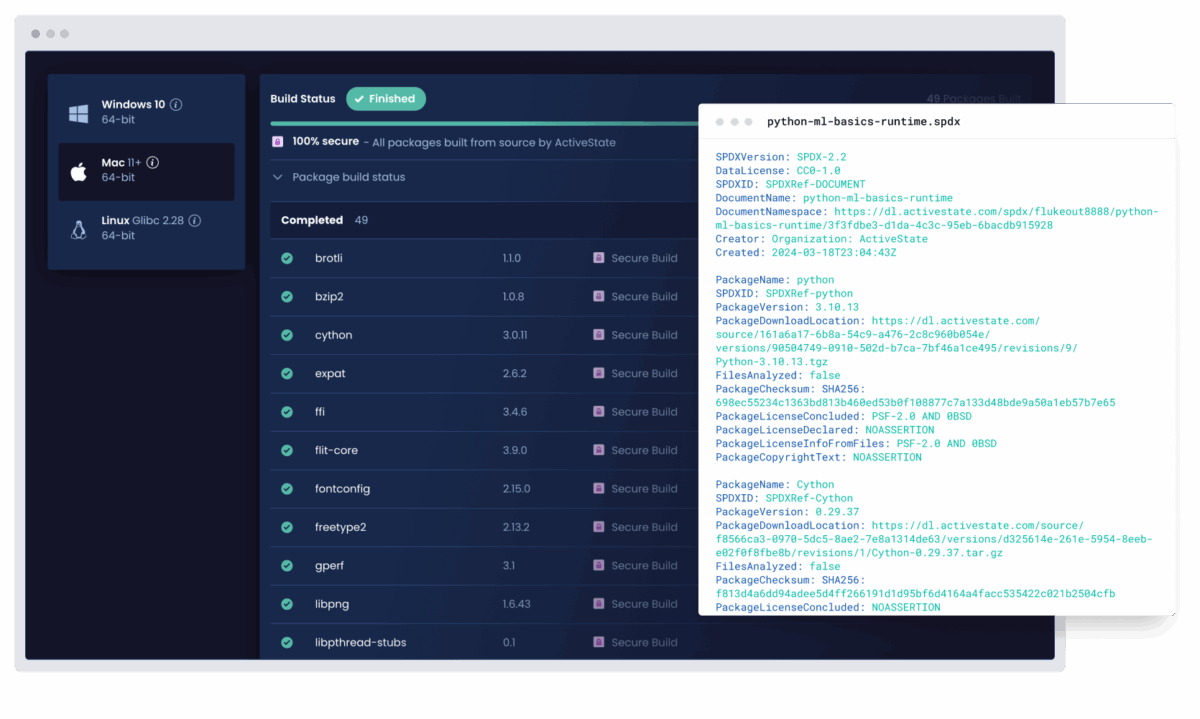
Enforce security policies and generate SBOMs automatically
Ensure every project meets your internal standards without adding extra manual work for developers.
Experience the ActiveState platform in action
Discover how to secure your software supply chain from source to deployment, all within a single platform.
In your demo, you’ll learn how to:
- Trace every component in your stack, including transitive dependencies
- Lock down builds with tamper-proof, secure build best practices
- Generate SBOMs, enforce policies, and prove provenance with ease
- Trace every component in your stack, including transitive dependencies
FAQs
How does the ActiveState platform help prevent supply chain attacks?
Our platform secures your software supply chain by providing complete visibility into all open-source components, automating vulnerability remediation with AI-powered prioritization, and ensuring secure, reproducible builds. This empowers enterprises and DevSecOps teams to proactively prevent attacks and ensure compliance from code to cloud.
What is a tamper-proof build pipeline?
It’s a reproducible, build-from-source process that guarantees what you ship is exactly what was built, all without hidden or modified components.
Can I detect vulnerabilities in transitive dependencies?
Yes. ActiveState scans all dependencies, which includes transitive ones. It does this to uncover hidden risks before they enter your CI/CD pipeline.
Will software supply chain security slow down my developers?
Not at all! Security is embedded early in the software development lifecycle, and the ActiveState platform automates policy checks, SBOMs, and compliance so your teams can move fast while staying secure.
Explore more resources

Supply Chain Security for FinServ
FinServ treats software supply chain security like reactive cybersecurity, making more work for AppSec. Learn how to be proactive instead.

Buyers Guide: Securing Your Software Supply Chain
Unravel the complexities of supply chain security with our in-depth whitepaper, meticulously crafted to empower your software development journey.

Software Supply Chain Security is a Dependency Management Problem
The pain of dependency management means vendors rarely update their apps leading to security issues. Learn how to automate dependency updates.



