Since open source software first arrived way back in the early 90’s, we’ve always expected just to download a prebuilt version of whichever dependency we require. But with the meteoric rise in software supply chain attacks over the past few years, pre-built dependencies may no longer be safe to use:
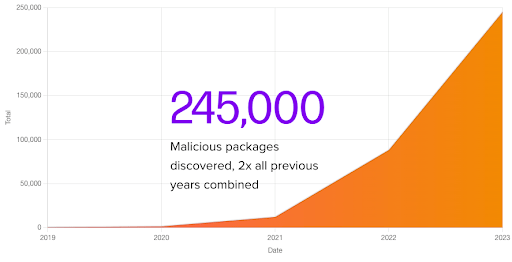
Source = Sonatype
To avoid the risk of downloading a malicious package from an open source repository we should be building them from source code. After all, building from source is the only way to guarantee the security of your third party dependencies. And as Sonatype reminds us:
“If you can’t effectively manage and ensure the security of your open source and third-party software, no other efforts made toward securing your supply chain will work — or frankly, even matter.”
But with the exception of security-conscious organizations like banks and certain government agencies, most of us are fine with trading security risks for the speed and convenience of prebuilt dependencies.
There can be any number of reasons for this kind of thinking, but generally it comes down to one or more of the following:
- Speed – anything that slows down development is a hindrance to achieving goals, which are typically measured in two week development sprints and quarterly business reviews.
- Growth – the majority of organizations are SMBs, and as such tend to be growth-oriented. Security is a drag on throughput, and therefore relegated to an afterthought, if it’s thought of at all.
- Selective Risk – many organizations build only a few, key dependencies (such as OpenSSL) from source, and are willing to live with the risk of using other, prebuilt dependencies.
- Competency – smaller organizations especially may lack the internal skills to build all their dependencies for all the operating systems they require.
- Costs – setting up a declarative, reproducible build system is a non-trivial undertaking, and can consume far more resources than most organizations realize – or can afford.
- Time – too many of the published instructions for building open source code from scratch are either woefully inadequate, out of date, or contain numerous errors. Correcting the build environment, editing the build script, and then debugging the build errors takes far more time than most are willing to invest.
But what if you could automate the build process for your dependencies?
How to Automatically Build Dependencies from Source Code
As I’ve discussed in a previous blog on Software Supply Chain Security for CI/CD Pipelines, it’s possible to implement a secure, SLSA-compliant, reproducible build system using many of the most popular CI/CD solutions.
But as I’ve also discussed in Best Practices: How To Update Your Codebase Without Breaking The Build, most organizations only ever build their open source dependencies once, and never update them. As such, creating a secure build system is overkill, and far from cost-effective.
This is why we built the ActiveState Platform: a SLSA Level 3-compliant secure build service that will automatically build your open source dependencies from source code (including linked C libraries) and package them as a runtime environment for Windows, Linux and macOS in just a few minutes.
There’s no need for expertise – just select the language, operating system(s) and dependencies your project requires (or upload the manifest file), and the ActiveState Platform will:
- Resolve all dependencies to ensure they work together without conflicts.
- Identify all vulnerable components BEFORE you run the build, so you can minimize the vulnerabilities your codebase starts with.
- Automatically build and package your dependencies as a runtime environment for your selected operating system(s).
- Allow you to share the runtime with all stakeholders, including fellow developers, QA teams, DevOps, etc to ensure everyone is using the same environment.
The process will also produce a Software Bill of Materials (SBOM) containing a complete list of dependencies generated at build time, as well as a Software Attestation you can use to prove that both the individual dependencies and overall runtime were built securely using a SLSA Level 3-compliant build service.
By automating your open source dependency builds in this way, even smaller organizations can afford to stop downloading risky, prebuilt dependencies and start ensuring their runtime environments are built securely from source code without wasting time, resources or money.
The following 4-minute video shows you exactly how the ActiveState Platform handles all the pain of environment setup and dependency building from scratch for you:
Next Steps:
Discover the ultimate solution for language version management with ActiveState’s Get Current, Stay Current. Say goodbye to dependency pains and hello to seamless coding. Click here to explore Get Current, Stay Current now!






