Software Composition Analysis
- Open source packages are viable for inclusion in your application’s codebase
- Open source licenses are approved for use, or else may be at odds with the overall license of your codebase
- Open source dependencies are affected by security vulnerabilities
The ActiveState Platform is a universal package management solution for Python, Perl and Tcl programming languages that provides organizations with the capabilities of software composition analysis (SCA) tools, including:
- A software Bill Of Materials (BOM) – a list of all packages and dependencies
- A Security Profile – a list of all known Common Vulnerabilities and Exposures (CVEs)
- License Compliance – a list of all known open source licenses in your codebase
By implementing the ActiveState Platform, organizations can centrally establish and maintain open source supply chain security across their extended enterprise, and empower security teams & DevSecOps to improve application security (appsec).
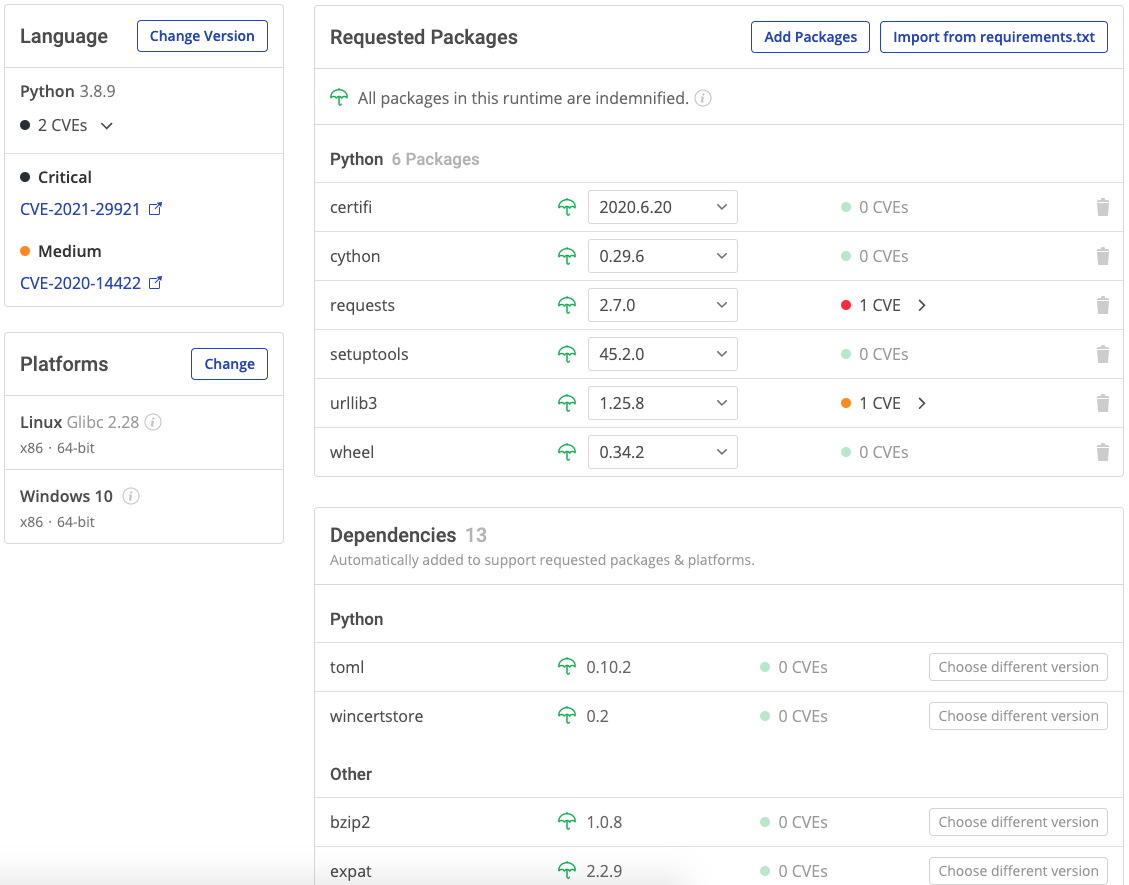
Software Bill of Materials
A BOM identifies all the open source packages and dependencies associated with your application, since you can’t manage what you don’t know you have. The BOM is key to identifying at a glance outliers, issues and errors that require further investigation on a per project basis.
The ActiveState Platform provides organizations with the capabilities of an open source compliance scanner. It delivers a comprehensive list of ingredients required to build your application, including:
- The version of the programming language for the project (Python, Perl and Tcl)
- Open source packages from the language’s ecosystem, as well as their dependencies
- Transitive dependencies (ie., dependencies of dependencies)
- Shared libraries (ie., OpenSSL, which is shared across all the platforms you support)
- Operating system (OS)-level dependencies
- Configurations (ie., metadata like version number, open source license, etc)
- A Common Vulnerabilities and Exposures (CVE) report, showing vulnerabilities for each component
A typical BOM might look like the following:
The BOM not only identifies all packages and dependencies, but also which ones have CVEs, as well as links to the National Vulnerability Database that explain each in detail.
Comply with Security Policies
With the escalating number of open source vulnerabilities reported over the past few years, keeping up with open source vulnerabilities has never been more difficult, or more important as cyber-attacks also continue to rise. But the Mean Time To Remediate (MTTR) vulnerabilities is often measured in weeks, if not months.
The ActiveState Platform not only builds all dependencies from source code for Windows, Linux and Mac, ensuring developers start with a secure development environment, but also provides organizations with the capabilities of an open source compliance scanner to help maintain security over time. The ActiveState Platform can help you reduce MTTR by providing:
- Status updates when your Python, Perl or Tcl environment is vulnerable, similar to GitHub
- A PDF report showing the severity level and details for each vulnerability
- The ability to fix and automatically rebuild your environment with secure open source components in minutes, speeding remediation
Because the ActiveState Platform tracks multiple versions of all your components, you can remediate vulnerabilities at the OS, package and dependency level by simply selecting a non-vulnerable version. The ActiveState Platform can save considerable time and effort by automatically rebuilding your environment, ready to be pulled into your CI/CD pipeline for testing.
See how it’s done in this 2-minute video.
A list of known vulnerabilities can also be generated using the ActiveState Platform’s command line interface (CLI), the State Tool.
Comply with Licensing Policies
Legal teams implement open source licensing policies to ensure against IP infringement and lawsuits. But identifying the licenses associated with every open source in component in your application can be difficult, since:
- Without a complete open source software bill of materials, you may miss some open source component and their licenses
- Components may have no stated license, increasing the risk of utilizing them
- Components may contain sub-components that have conflicting licenses, making it difficult to understand whether the overall license complies with your policy
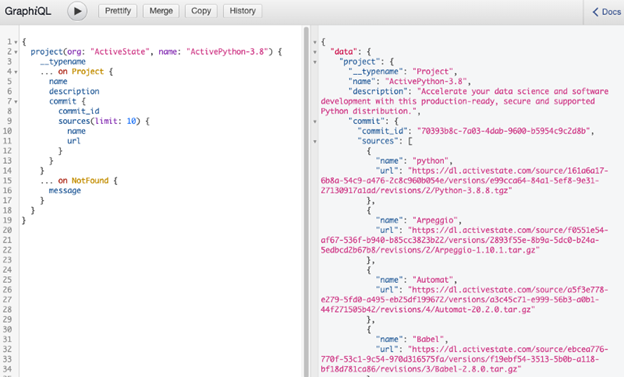
The ActiveState Platform can help you mitigate license risk by providing a complete bill of materials, and the licenses associated with them. You can use the ActiveState Platform’s API to programmatically retrieve and identify the licenses associated with every open source component in a project’s codebase, allowing you to automate open source license compliance.
For example, running a license API query on our ActivePython project returns:
Ready to see for yourself? You can try the ActiveState Platform by signing up for a free account using your email or GitHub credentials. Or sign up for a free demo and let us show you how you can implement secure dependency scanning in your organization.
Frequently Asked Questions
What is SCA tool?
- Ensure license compliance in order to mitigate the risk of IP lawsuits
- Ensure security by identifying the number and severity level of vulnerabilities
- Create a software bill of materials in order to identify and track all open source components in their applications
Software composition analysis tools like the ActiveState Platform can be used for these purposes, while letting every stakeholder in the enterprise monitor the risk associated with the open source they use. Sign up for a free account to try out the ActiveState Platform, or sign up for a free demo and let us show you how it works.
What is software composition analysis?
- A software bill of materials for all dependencies
- Open source license(s) per component
- A list of the security vulnerabilities showing the severity level for each open source component
The ActiveState Platform provides all the capabilities of a software composition analysis tool for Python, Perl and Tcl projects. Sign up for a free account to try it out, or sign up for a free demo and let us show you how it works
What is SCA in security?
Software composition analysis (SCA) for security refers to the ability to identify open source vulnerabilities that may affect the security of your application. SCA tools identify Common Vulnerabilities and Exposures (CVEs) for every open source component in your application, which are designated with a severity rating ranging from none to low to medium, high and critical.
The ActiveState Platform can provide organizations with the ability to identify the security status for all Python, Perl and Tcl open source components. To understand how the ActiveState Platform can help you identify and remediate security vulnerabilities, read How To Remediate Your Open Source Vulnerabilities Quicker
When can I use software composition analysis?
- Open source vulnerability information
- Open source licenses embedded in your application’s code
- All the open source components that comprise an application.
The software composition analysis tool can then provide you with a report that shows:
- Vulnerabilities per dependencies, as well as their severity rating
- Open source licenses associated with each dependency
- A software bill of materials that contains a complete list of all dependencies in your application
For more information, read our Open Source And The Visibility Problem blog.