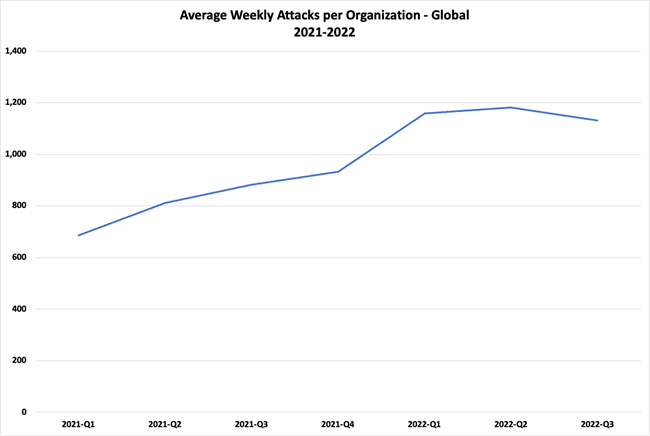
For example, Check Point Research notes that cyberattacks showed a 28% growth year-on-year in 3Q22, with more than 1130 average weekly attacks/org worldwide.
Figure 1: Avg Weekly Cyberatttacks. Source = Check Point Research
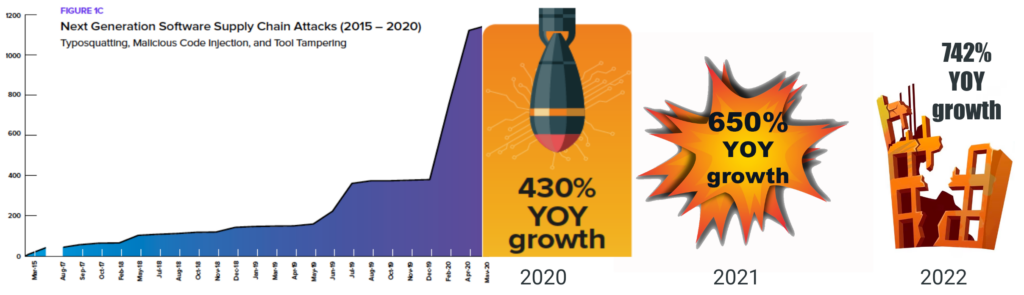
Ransomware remained a key threat in 2022, but while organizations were focused on network security, they likely missed the fact that cyberattacks have shifted from targeting applications to compromising open source software components. In fact, open source software supply chain exploits have grown by 742% over the past three years.
JavaScript and Python, as two of the world’s most popular programming languages, have borne much of the brunt of this supply chain disruption. Attacks on their respective public repositories, npm and PyPI have grown 289% since 2018, forcing the removal of thousands of compromised packages designed to mine cryptocurrency, steal credentials or plant malware, among other threats.
But 2022 was also notable for a number of other initiatives that gained significant traction, including the release of new AI tools and a security framework that can help us all get our software supply chain in order. Let’s dig in.
US Secures the Software Supply Chain
Thanks to the pandemic’s disruption of worldwide manufacturing supply chains, everyone knows how interlinked the chain of raw materials-> manufacturer -> shipper -> consumer truly is. However, most of us weren’t introduced to how interlinked the software supply chain is until 2021 when President Biden followed up the Solarwinds cyberattack by issuing “Executive Order 14028,” which focused on how organizations could improve the security of their software supply chain.
Last year, EO 14028 was back in the news in September when the US government imposed an accelerated timeline for Independent Software Vendors (ISVs) to secure their software supply chain if they hope to continue selling to US government departments and agencies.
Essentially, the US government, long a target of hackers, has finally declared war on the lack of security in the software supply chain in general, and the open source supply chain specifically. The problem has compounded since the pandemic when hackers began to realize the economies of scale that can be derived from compromising a single popular open source component used by the thousands of software vendors with tens of thousands of customers: a single exploit could potentially provide access to millions of compromised organizations.
Figure 2: Growth of Software Supply Chain Attacks
Based on the difficulties companies have had managing their software supply chain to date, 2022 saw an explosion in the purchase of cyber insurance in order to help organizations mitigate the cost of a cybersecurity incident. But given that there’s less than 150 days left for US government ISVs to secure their software supply chain, a better strategy would be investing that money in prevention instead.
For example, ISVs should focus on three key aspects that can help them and their customers address the weaknesses in their software supply chains:
- SBOMs – provide an “ingredients list” of all the components that make up a software application.
- Software Attestations – provide metadata that can be used to independently validate the security and integrity of an application.
- Secure Software Development – specifically, adoption of the secure software development frameworks published by the US National Institute of Standards and Technology (NIST)
The AI Revolution
While Artificial Intelligence (AI) capabilities now come embedded in many of the tools organizations have been using for years (typically introduced as Machine Learning tasks created with open source languages like Python to help increase efficiency and lower costs), there are a number of new tools that exploded onto the scene in 2022, including:
- AI Text Generators – from chatGPT to Jasper to Neuroflash, these AI writer tools allow organizations to generate everything from blogs to product descriptions to social media posts and email communications in multiple languages, enabling organizations to generate more content for less.
- Text-to-Image Generators – from Stable Diffusion to Midjourney to DALL-E, the ability to automatically generate an image from a descriptive sentence has enabled organizations to replace stock photography subscriptions. More pertinently, add ons like SlidesAI lets you automatically generate Google slides from text prompts, including graphics.
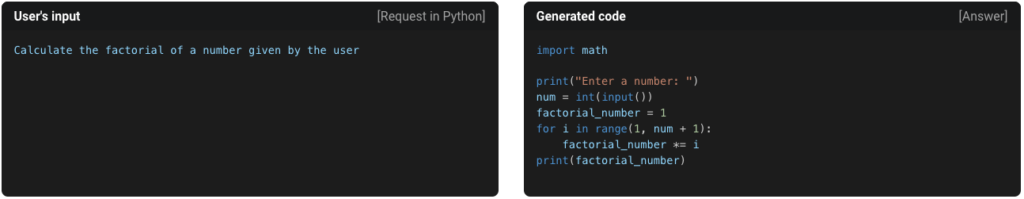
- Code Generators – AI-based code completion tools like GitHub’s Copilot, Tabnine and Salesforce’s CodeT5 have already proven to be extremely effective at “filling in the blanks” based on your existing code. But wholesale code generation from scratch is the goal of new tools like Open AI’s chatGPT, SourceAI and DeepMind’s AlphaCode.
Figure 3: Text-to-code example. Source = https://sourceai.dev/
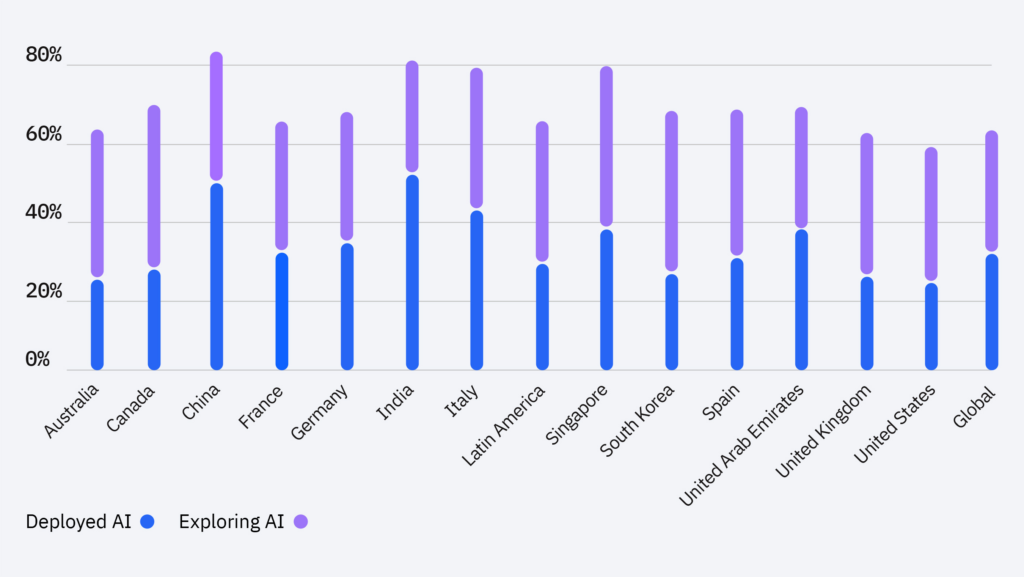
While these kinds of AI tools are incredibly empowering for users at this point in time, the reality is that “one worker, equipped with the right prompts, could bear the same workload as 7, in half the time.” It’s this kind of ROI that’s driving corporate interest worldwide:
Figure 4: AI adoption. Source = IBM Global AI Adoption Index
For those organizations that have borne the brunt of The Great Resignation in 2022, as well as for those left struggling following the latest round of Tech layoffs so far in 2023, AI may seem like a saving grace.
If you’re trying to do more with less, here are some key resources that can help:
- Watch our Webinar: Keeping Software Devs Happy by Automating Open Source Pains
- Learn how our Managed Open Source Distributions can help minimize developer team workloads.
Supply chain Levels for Software Artifacts (SLSA)
Google originally launched their SLSA initiative internally as a way to establish trust for both the proprietary and open source code their developer used. Like most software organizations, they had any number of methodologies and tools to help them profile the components in their software, but very few that allowed them to demonstrate the degree of security stringency for each. As a result, software companies continue to:
- Import compromised open source components from npm, PyPI, RubyGems, etc.
- Build software with bad dependencies.
- Ship compromised software to customers.
In late 2022, however, Google handed the SLSA initiative over to an industry consortium who finalized the very first version. Now every organization has a standard way to ensure developers, ISVs and other organizations are creating safe software from secure components, while also ensuring bad actors have fewer holes to exploit with ransomware, malware infections and other cyberattacks.
The SLSA framework offers several maturity levels for security-conscious organizations to aspire to, but even attaining just SLSA Level 2 can mean your processes are in very good shape:
| Level | What Is Involved? |
| 0 | There are no security and integrity guarantees wrt to built artifacts. SLSA 0 is where most organizations will find themselves starting out. |
| 1 | The build process must be fully scripted/automated and generate provenance. |
| 2 | The source code must be version controlled, and the automation scripts for the build must be run by some kind of dedicated build service. |
| 3 | A few additional standards are added into the mix, but the big jump to get to SLSA 3 is moving from self-auditing to being audited by an external auditor. |
| 4 | To reach level 4, you must have the rest of the specifications in place, such as two-person code reviews. In addition, all builds must be reproducible. |
SLSA may seem daunting at first glance, but it really won’t take much for most organizations to get to Level 2. Any organization that uses modern application development practices, and has a CI/CD pipeline in place has already laid much of the required groundwork, allowing you to focus on the extra features.
Some good places to start include:
- The basics: What Are Supply Chain Levels for Software Artifacts (SLSA)?
- Learn How to Secure Your Software Builds with SLSA
- Watch our Webinar: DevOps, SLSA and Software Supply Chain Security
Conclusions
DevSecOps has been on the cusp of becoming the norm for software organizations for more than a decade, but security has always taken a back seat to closing market gaps with new features.
Now, with the US government imposing deadlines in 2023 for organizations to secure their software supply chain, DevSecOps will need to be THE priority if ISVs want to continue selling to the US government. US government vendors include thousands of software companies, but even those ISVs that do not sell to US departments and agencies should be aware that US government standards often end up as general industry requirements, as well.
Frameworks like SLSA can help ISVs fast track software supply chain security, as can the ActiveState Platform, which offers a zero-config, cross-platform build service for open source language runtimes. The ActiveState Platform’s secure build service provides controls to meet SLSA Level 4 standards, while delivering SBOMs and software attestations to help decrease the cost and risk of working with open source dependencies.
Next steps:
Learn how you can gain all the benefits of SLSA with none of the work by leveraging the ActiveState Platform.
Read Similar Stories

The US government secure supply chain deadline for SBOMs and software attestations is June 2023. Find out how to meet the date.

Learn how to comply with US government secure supply chain & software development requirements, including software attestations and SBOMs.

The US Government requires software vendors to provide self-attestation. Learn what attestations are and how to navigate these restrictions.