Home > Solutions > Software Supply Chain Security > Open Source Dependency Scanner
Open Source Dependency Scanner
Open source dependencies make up the majority of the code in any modern web application, but working with them poses a number of challenges, including:
 Ensure your development process is secure from the first line of code.
Ensure your development process is secure from the first line of code.
 Unlike other dependency scanners, ActiveState Platform will show you the implications of selecting a new version of a dependency on all the other components of your environment BEFORE you commit to it. Never break your environment again!
Watch this video to learn how to use the ActiveState Platform to remediate vulnerable Python, Perl and Tcl runtime environments by selecting non-vulnerable package versions, and automatically rebuilding your environment, helping to shortcut the lengthy remediation process.
Unlike other dependency scanners, ActiveState Platform will show you the implications of selecting a new version of a dependency on all the other components of your environment BEFORE you commit to it. Never break your environment again!
Watch this video to learn how to use the ActiveState Platform to remediate vulnerable Python, Perl and Tcl runtime environments by selecting non-vulnerable package versions, and automatically rebuilding your environment, helping to shortcut the lengthy remediation process.
- Security Awareness – how do you know which dependencies of your open source code are vulnerable? And which are false positives.
- Vulnerability Remediation – how can you resolve vulnerabilities in a timely manner?
- License Compliance – how do you know if all your dependencies feature licenses that are compatible with your corporate guidelines?
- Build from Source Code: Know exactly what’s in your code across your entire software development lifecycle (SDLC) from your development environment through CI/CD to production.
- Resolve Vulnerabilities: Find, fix and automatically rebuild vulnerable Python, Perl and Tcl runtime environments for your open source projects.
- Ensure Compliance: Get detailed licensing reports and a Bill of Materials (BoM) for all the dependencies in your code.
Security-First Dependency Management
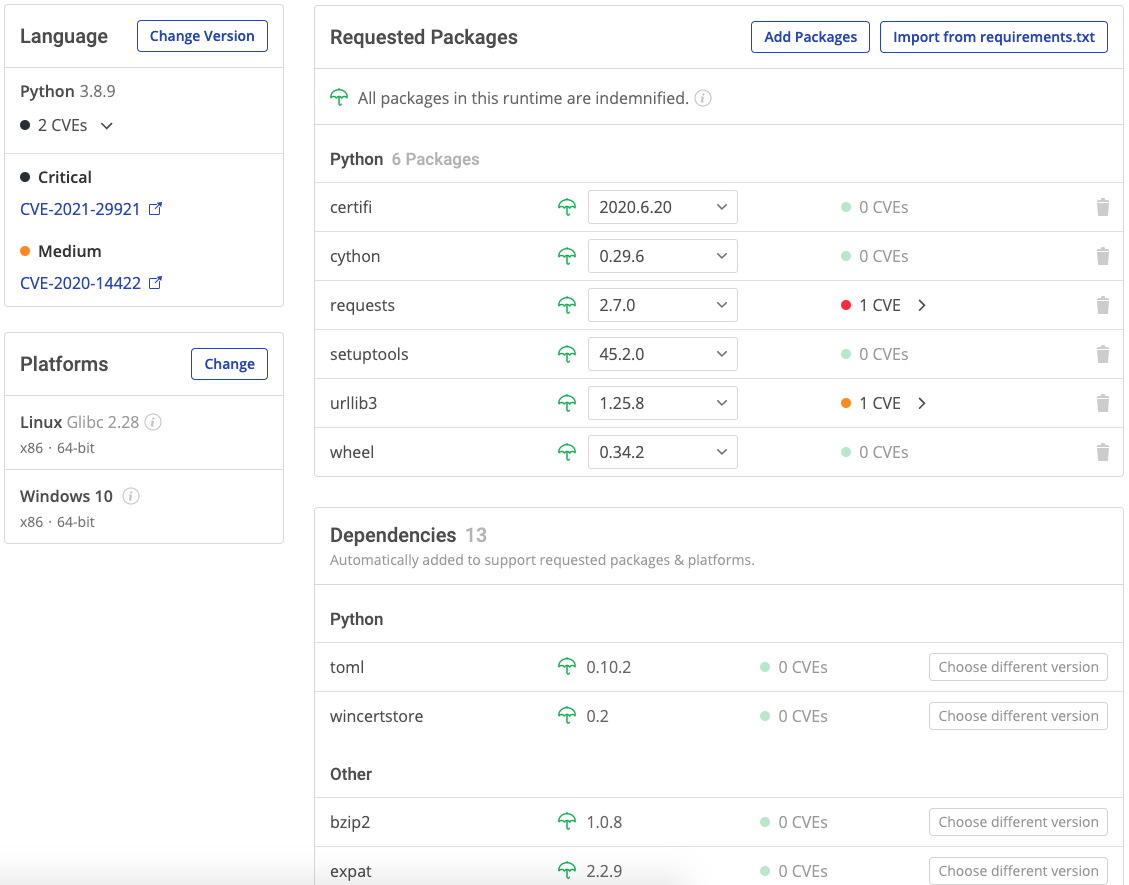
The ActiveState Platform is an all-in-one package management and risk management solution for open source languages:- Development and DevOps teams can improve the security and reduce the complexity of the Python, Perl and Tcl environments they’re using to build their applications.
- Security & Compliance teams can reduce risk with better oversight and maintenance of all open source components.
- Pull in and resolve all dependencies, providing your with a complete software BoM, including:
- Transitive dependencies (ie., dependencies of dependencies)
- OS-level dependencies
- Shared dependencies (ie., OpenSSL)
- Environment dependency-checks flag any Common Vulnerabilities and Exposures (CVEs), providing you with severity level for each along with a link to the National Vulnerability Database (NVD) so you can read further details
- Build everything from source code in parallel in just a few minutes
- Package your environment for deployment on Windows, Linux or Mac
 Ensure your development process is secure from the first line of code.
Ensure your development process is secure from the first line of code.
Remediate Vulnerabilities Faster
Resolving an open source vulnerability shouldn’t take weeks. With the ActiveState Platform, you can identify and replace vulnerable packages, and then follow the workflow to automatically rebuild your Python, Perl and Tcl environments for Windows, Linux or Mac in minutes. The ActiveState Platform acts as a single source of truth for your Python, Perl and Tcl environments. Remediate security vulnerabilities once, and secure your development, CI/CD and production environments. Security Status: Identify the number and severity of CVEs in your projects via web, command line (CLI) or API. New vulnerabilities are flagged every 24 hours. Security Reports: email-able PDF reports provide details of each vulnerable dependency, allowing you to make every stakeholder in your organization aware. Vulnerability Remediation: interactive Python, Perl and Tcl environment configurations allow you to find and fix known vulnerabilities by upgrading or downgrading vulnerable components to secure versions.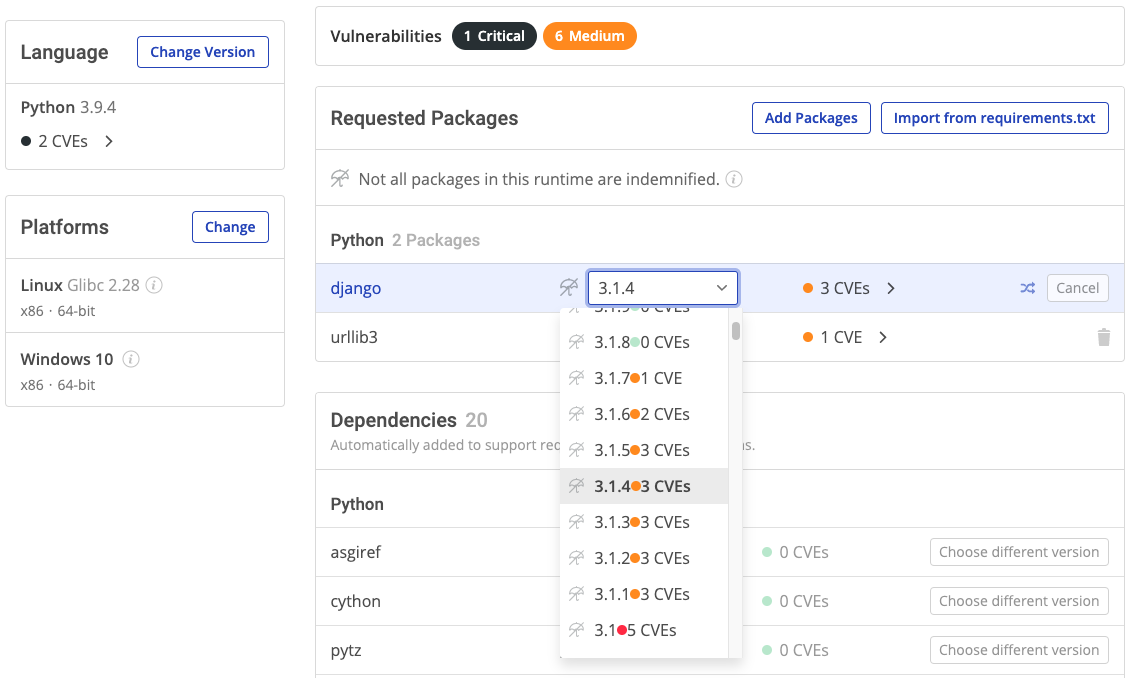 Unlike other dependency scanners, ActiveState Platform will show you the implications of selecting a new version of a dependency on all the other components of your environment BEFORE you commit to it. Never break your environment again!
Watch this video to learn how to use the ActiveState Platform to remediate vulnerable Python, Perl and Tcl runtime environments by selecting non-vulnerable package versions, and automatically rebuilding your environment, helping to shortcut the lengthy remediation process.
Unlike other dependency scanners, ActiveState Platform will show you the implications of selecting a new version of a dependency on all the other components of your environment BEFORE you commit to it. Never break your environment again!
Watch this video to learn how to use the ActiveState Platform to remediate vulnerable Python, Perl and Tcl runtime environments by selecting non-vulnerable package versions, and automatically rebuilding your environment, helping to shortcut the lengthy remediation process.
Ensure Open Source License Compliance
Reduce licensing risks by ensuring that developers are only using properly-licensed third-party dependencies. And minimize exposure if things do go wrong. Let ActiveState help you reduce your reliance on software audits.- Ensure only open source dependencies with approved licenses are available for use in your Python, Perl and Tcl development environments.
- Get access to licensing reports that let Compliance teams know what you plan to distribute or put into production.
- Gain a Bill of Materials view of every open source component included in your application to ensure nothing slips through the cracks.
Frequently Asked Questions
What is an Open Source Dependency Scanner?
Open source dependency scanners are primarily used to:
- Identify vulnerabilities in packages and dependencies
- Identify open source licenses associated with each package and dependency
- Provide a software bill of materials for your application
How does an Open Source Dependency Scanner work?
Open source dependency scanners rely on three tools:
- The National Vulnerability Database (among other sources), which provides dependency vulnerability information.
- A source code scanning tool that identifies open source licenses embedded in the code.
- A software composition analysis tool that identifies all the open source components that comprise an application.
- Vulnerabilities in packages and dependencies
- Open source licenses associated with each package and dependency
- A software bill of materials for your application
What is an Open Source Dependency Scanner?
A dependency checker (also known as a dependency scanner or software composition analysis tool) is used to identify vulnerabilities in open source software. The checker will typically provide:
- A list of all open source dependencies in your application
- The severity level of each vulnerability
- Links to details about each vulnerability
How do I run a Dependency Scanner?
Dependency scanners are typically run either as part of a source code repository (ie., GitHub), or else during the CI/CD process (ie., Black Duck).
- Repository Scanning – dependencies are automatically monitored for vulnerabilities and a notification provided when one is discovered.
- CI/CD Scanning – whenever the CI/CD process is run, an instance of the application is spun up and scanned. Generally, the scan creates a report that must be subsequently examined and investigated.



